Secure everything, everywhere. Squared!
Written by Dominik Joe Pantůček on 2016-09-27
securityI was really keen to attend one of the (ISC)2 SecureEvents: The SecureCEE Conference 2016 in Prague. Read on if you are interested in current security trends!
After the obligatory introduction of the host – PricewaterhouseCoopers – and an informative talk about the (ISC)2 itself and about the current development in the EMEA region by Adrian Davis, the actual technical talks started.
Michal Čábela’s talk did not convince me I am using IoT when – in fact – I am not. But the very next talk got my attention.
Paolo Ottolino talked about web 2.0 in really refreshing way. As a speaker, he could really use some coaching (who of us could not), but he did a great job in stripping all of that anything-2.0 buzzword-filled stuff off and got down to the core of the topic: always do a risk analysis, choose the right tools and check what others are doing and using. A question from the audience challenged the very basis of his talk: why should we use what others use and there are many people looking for flaws in such software?
Security through obscurity has never worked, it does not and it never will! Bear this in mind when choosing what to use.
If you want to sell anything these days, put an IoT sticker on it. Yes, the Internet of insecure Things. Add privileged access to the mix and you are ready for failure of grandiose scale. By example of taking down part of the electricity distribution grid in Ukraine, Daniel showed the old truth – the more possible attack vectors, the worse the impact of a single breach can be. Especially if you have a well-organized adversary willing to orchestrate an attack using all the vulnerable resources available.
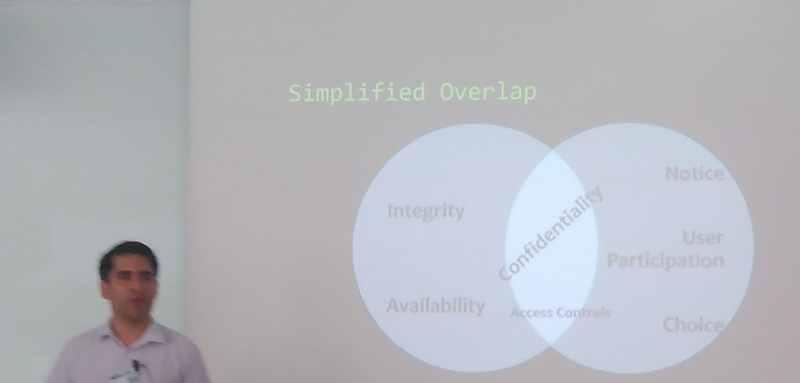
This report is actually an school assignment given to me by my former thesis advisor and my current teacher – your favorite security expert, czexican Jorge. What if I fall asleep during his talk?
Truth is, Jorge rocked the stage. Literally. If you – as a developer or service provider – actually care, you can add the privacy to the regular mix of user experience, business relevance and – you probably guessed this one – security. I tried to respect his privacy and took only a blurry picture of his face – yet got one of his most important slides perfectly sharp!
But seriously, look up something about OECD privacy principles and just think about them for awhile. Or think about different layers of personal information going from sensitive personal information way out to anonymous statistics. Maybe the whole “privacy by design” is not just another buzzword for the PR department. But who knows...
Then just the (ISC)2 Czech chapter update filler before the lunch break. Due to the lack of tables, choosing a goulash with dumplings was definitely not the best decision some speakers made.
It is sad Bruce Hallas’ talk was scheduled immediately after the lunch. It was an energetic talk and yet my head was falling down all the time. Bruce, if you are reading this, I am sorry – but we can both blame the organizers, cannot we?
The following talk found most of the audience more awake which was great, because the presentation of Darktrace by Sam Adlerman-Miller contained some really under-the-hood information about their self-learning technologies.

Afternoon refreshments[1] did their job and after the break, back in the auditorium, most attendees found themselves in quite cheery mood.
With a honey cake and a cup of tea on my table I was ready for the next talk – given by Matteo Ferraroni – that focused mostly on the biggest security threat: the human factor.
Lastly, in the panel discussion, Jorge slightly disappointed me. One of the first questions was about how you deploy your infrastructure in cloud with respect to security and your company security directives. It is a pity Jorge did not mention my thesis for which he has been an advisor. It attempts to answer these questions with rigorous approach using readily-available standards and guidelines provided for example by NIST.
At the end of the day, my feelings are basically: when does the next (ISC)2 conference take place? Go there! I definitely will, if I can.
- Free Food, It binds us.: A proximity-triggered model for characterizing nano-informatic structures. Cham, J. G.*, Slackenerny, M. A. and Smith, B. S. *California University of Technology, Pasadena, CA Stanford Institute Center, Palo Alto, CA, available at http://www.phdcomics.com/archive_journal.php?n=39
