Email quest - part 2
Written by Dominik Joe Pantůček on 2018-02-15
emailAfter venturing into the basic architecture of a robust email solution last week, we will look into the remaining missing bits today. Then we should look for some answers about how to secure the email communication end-to-end. In this article we find anti-spam and anti-virus solution integrated into our infrastructure, configure server-side filters, add DKIM[1] signing and verification and give our users nice webmail interface to use.
Amavis: Anti-spam and anti-virus
In order to protect our users from malicious programs distributed by unsolicited email and also to shield them from the burden of finding legitimate email in their mailboxes, we use amavisd-new[2] software package which can integrate multiple filtering and scoring solutions into one email proxy that can flag or ultimately drop emails based on a predefined set of tests. For our anti-spam solution we use Apache SpamAssassin[3] and to protect against malicious software we leverage the ClamAV[4] antivirus.
We can install all of them pretty simply:
yum install amavisd-new spamassassin clamav
First, we configure SpamAssassin. Contrary to the default installation, we want to run the SpamAssassin daemon under separate user from the start as it processes potentially untrusted data. We prepare a user for that:
groupadd spamd
useradd -g spamd -s /bin/false -d /var/log/spamassassin spamd
chown spamd:spamd /var/log/spamassassin
Then update start options of the daemon in
/etc/sysconfig/spamassasin:
SPAMDOPTIONS="-d -c -m5 -H -u spamd"
And start it:
systemctl enable spamassassin
systemctl start spamassassin
Now we are ready to configure ClamAV. There are actually two components that need to
be configured. Firstly the ClamAV daemon itself and secondly the freshclam service that
ensure the latest virus database is always available to it. ClamAV scanning service is
configured in /etc/clamd.d/scan.conf and basically the following is
sufficient:
DatabaseDirectory /var/lib/clamav
LocalSocket /var/run/clamd.scan/clamd.sock
ScanMail yes
And of course, we start the daemon:
systemctl enable clamd@scan
systemctl start clamd@scan
For the freshclam service, everything should be ready and we just need to enable and start it:
systemctl enable clam-freshclam
systemctl start clam-freshclam
Integrating anti-spam and anti-virus using amavisd-new into postfix[5] is pretty
easy. We setup the general amavisd-new service in
/etc/amavisd/amavisd.conf, by adding the following modifications:
$mydomain = 'trustica.cz';
$myhostname = 'mailserver.trustica.cz';
$notify_method = 'smtp:[127.0.0.1]:10025';
$forward_method = 'smtp:[127.0.0.1]:10025'; # set to undef with milter!
And, once again, just start the service:
systemctl enable amavisd
systemctl start amavisd
On the postfix side of the email queue, we tell it to pass all incoming email to
amavisd-new for filtering by adding the following configuration to
/etc/postfix/main.cf:
content_filter=smtp-amavis:[127.0.0.1]:10024
In the /etc/postfix/master.cf configuration file we add stanza for the return receiver on TCP[6] port 10025 with content_filter option disabled:
127.0.0.1:10025 inet n - n - - smtpd
-o content_filter=
And then only restart postfix to start using our amavisd-new with anti-virus and anti-spam filters:
systemctl restart postfix
This is it. We have protected our users against spam and viruses (mostly).
Server-side filters in dovecot
Many users do not realize it as they see email filtering of any email solution they use, but for both common cases - either using web mail or desktop mail user agent - there are many benefits of server-side filtering. To integrate it seamlessly into both solutions, the delivery agent and IMAP[7] server must do it the right way. The current Internet standard for email filtering is the Sieve[8] protocol and language.
For dovecot[9], there is a Sieve implementation called pigeonhole. Wouldn't it be nice if those pigeons delivering your messages would also do some filtering based on your preferences and - for example - spam checking which has taken place just before email delivery? We install the plugin easily:
yum install dovecot-pigeonhole
To configure it, we need to ensure the following directives are present in dovecot configuration:
mail_plugins = $mail_plugins imap_stats imap_sieve
sieve_plugins = sieve_imapsieve
And then just restart the dovecot service:
systemctl restart dovecot
Now it is possible to configure your server-side filters using either your favorite mail client plugin or you can wait for web mail to be configured and use web-based administration interface provided there.
DKIM signing
To add DKIM signatures to outgoing emails - for configured domains - and to verify signatures of incoming email messages, we use OpenDKIM[10]. It can be easily installed with:
yum install opendkim
With OpenDKIM installed, we create our default signing key by issuing the following commands:
opendkim-default-keygen
This generates the signing key in /etc/opendkim/keys/default.txt. We
can change the comment to reflect our system name, but the important part is the key
anyway.
As we will use OpenDKIM for both signing and verification and we want to use it for signing email messages of multiple domains, the following configuration prepares everything for us:
Mode sv
Socket inet:8891@localhost
Canonicalization relaxed/simple
KeyTable refile:/etc/opendkim/KeyTable
SigningTable refile:/etc/opendkim/SigningTable
ExternalIgnoreList refile:/etc/opendkim/TrustedHosts
InternalHosts refile:/etc/opendkim/TrustedHosts
Mode directive tells OpenDKIM to process both outgoing emails by adding DKIM signature as instructed in key and signing tables and verifying incoming emails containing DKIM signatures. The key and signing tables map keys and domains, so we can use single key for signing messages from multiple domains and we can also use multiple signing keys on our system. OpenDKIM documentation gives more detailed information on this.
Technically speaking OpenDKIM implements "milter"[11] - that is
sendmail[12]-compatible filter that gets a message plus some meta information,
processes the message and returns the result to the calling process. Connecting postfix
to milter is really straightforward and can be achieved by adding the following to
/etc/postfix/main.cf configuration file:
smtpd_milters = inet:127.0.0.1:8891
non_smtpd_milters = $smtpd_milters
milter_default_action = accept
Now we just enable and start OpenDKIM daemon and restart postfix:
systemctl enable opendkim
systemctl start opendkim
systemctl restart postfix
And this is it. We are signing outgoing messages as specified in key and signing tables and we are able to use OpenDKIM daemon for verifying incoming messages' DKIM signatures.
Webmail
The simplest way of installing Roundcube[13] web mail is the same way as installing postfixadmin[14]. We download the distribution tarball, unpack it to designated directory in our webserver document root and change access rights in order to ensure the HTTP server process can write to required subdirectories:
wget http://nchc.dl.sourceforge.net/project/roundcubemail/roundcubemail/1.1.3/roundcubemail-1.1.3-complete.tar.gz
tar -zxvf roundcubemail-1.1.3-complete.tar.gz -C /var/www/html
mv /var/www/html/roundcubemail-1.1.3/ /var/www/html/roundcube
chown apache:apache /var/www/html/roundcube/temp/
chown apache:apache /var/www/html/roundcube/logs/
chcon -t httpd_sys_content_rw_t /var/www/html/roundcube/temp/
chcon -t httpd_sys_content_rw_t /var/www/html/roundcube/logs/
As with postfixadmin, Roundcube comes with web-based installer and we launch it by pointing our favorite web browser to https://mailserver.trustica.cz/roundcube/installer. During the installation we chose to install jqueryui, managesieve and password plugins. Sometimes, there are problems with PHP[15] installation concerning date formatting and time zone. This is especially true for example with Czech locales. We fix this by adding the following to php.ini file:
date.timezone = "Europe/Prague"
The directive should match system time zone.
As we have installed plugins for password changing and managing sieve filters, we need to allow the HTTP server process to connect to TCP sockets as all the management is done over TCP - although only locally in our case:
setsebool -P httpd_can_network_connect=1
systemctl restart httpd
It is also advisable to run Roundcube database cleaning job regularly by adding the following to crontab[16]:
0 0 * * * apache bash /var/www/roundcube/bin/cleandb.sh > /dev/null 2>&1
And this is it, your users have web-based email client available at https://mailserver.trustica.cz/roundcube and they are able to use it for changing their passwords and managing server-side sieve filters.
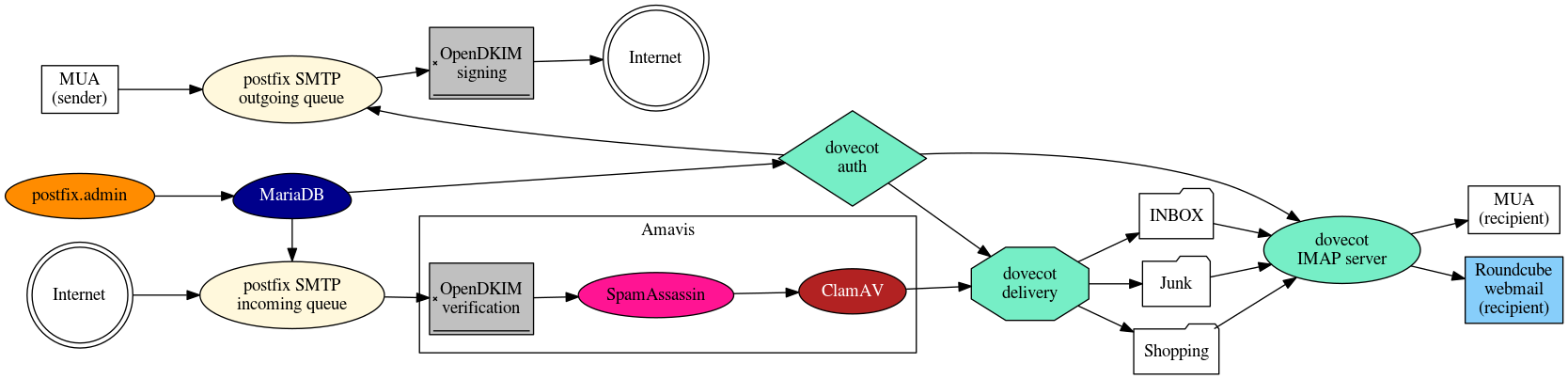
Picture 1: Overall architecture of the system. In this series we have looked at how complex can email communication become if you do it properly. We have also shown it is very robust communication platform and next week we are about to talk more about securing email communication end-to-end with no compromises. See you next week!
References
-
RFC 4870: Domain-Based Email Authentication Using Public Keys Advertised in the DNS (DomainKeys), Network Working Group, May 2007, available online at https://tools.ietf.org/html/rfc4870
-
amavisd-new, official homepage available at https://amavis.org/
-
Apache SpamAssassin, official homepage available at https://spamassassin.apache.org/
-
ClamAV antivirus, official homepage available at https://www.clamav.net/
-
Postfix, Wietse Venema's mailserver, official homepage available at http://www.postfix.org/
-
RFC 793: TRANSMISSION CONTROL PROTOCOL, Defense Advanced Research Projects Agency, Information Processing Techniques Office, September, 1981, available online at https://tools.ietf.org/html/rfc793
-
RFC 1730: INTERNET MESSAGE ACCESS PROTOCOL - VERSION 4, Network Working Group, December 1994, available online at https://tools.ietf.org/html/rfc1730
-
RFC 3028: Sieve: A Mail Filtering Language, Network Working Group, January, 2001, available online at https://tools.ietf.org/html/rfc3028
-
Dovecot, secure IMAP server, official homepage available at https://www.dovecot.org/
-
OpenDKIM, official homepage available at http://www.opendkim.org/
-
Milter. (2018, January 6). In Wikipedia, The Free Encyclopedia. Retrieved 19:15, January 21, 2018, from https://en.wikipedia.org/w/index.php?title=Milter&oldid=819020086
-
Sendmail. (2017, October 28). In Wikipedia, The Free Encyclopedia. Retrieved 19:16, January 21, 2018, from https://en.wikipedia.org/w/index.php?title=Sendmail&oldid=807511570
-
Roundcube, open source webmail software, official homepage available at https://roundcube.net/
-
postfix.admin, official homepage available at http://postfixadmin.sourceforge.net/
-
PHP: Hypertext Preprocessor, available online at https://secure.php.net/
-
Cron. (2018, January 11). In Wikipedia, The Free Encyclopedia. Retrieved 19:18, January 21, 2018, from https://en.wikipedia.org/w/index.php?title=Cron&oldid=819898936
