Casual email communication
Written by Dominik Joe Pantůček on 2018-05-24
emailAfter ranting about elliptic curves for more than three months, it is probably the time to pause for awhile and think where the encryption based on elliptic curves of some kind might be really needed. Although many people might disagree, for some of us, liberating the communication between people is the most important thing the Internet brought. And although the generic data communication by transferring data packets over the network do not provide much convenience to an ordinary human being, if we look at some real human-to-human communication on the Internet, the email fits in really well. It has its quirks - but what does not?
I know, I know - you are here just for the video, are you? I would suggest reading the backstory first, but if you insist, here it is.
Walking through the history[1][2][3], we have learned about email[4]. We went on a quest for perfect email server[5][6] and stopped before thinking about end-to-end security of the email communication. Now it is the time to go back and look exactly at that. How secure the email communication really is? How do you trust your email provider? Your server administrators? So many questions - but not many answers.
Let us try to give you some insight using an email soap opera story. You have already met Alice and Bob and it turns out, there is more to them.
Ideal world
In the ideal world, everything works as expected. Alice sends a message to Bob confirming their tomorrow evening date. Bob receives the email and everyone is happy. But that would be rather short soap opera. And if you look at picture 1, quite boring one it truly is.

Picture 1: Casual email communication in an ideal world. But the world is not always ideal...
Real world
You might encounter all sorts of problems in the real world. For example evil Eve, that tries to eavesdrop the communication between Alice and Bob. Or even worse, she might want to modify the message in transit and cause quite some trouble that way.
Although nowadays the SMTP[7] connections are usually protected by TLS[8] encryption, virtually no SMTP server bothers verifying the certificates. Therefore if an attacker can modify the data traffic, it is possible to modify the actual messages as well. The same applies for SMTP servers someone broke into or those where their administrators cannot be trusted.
As you can see in Picture 2, the situation is slightly hazy in the real world. And even though it is just our email soap opera, these things can happen and actually happen pretty often. The worst thing is, that usually nobody notices.
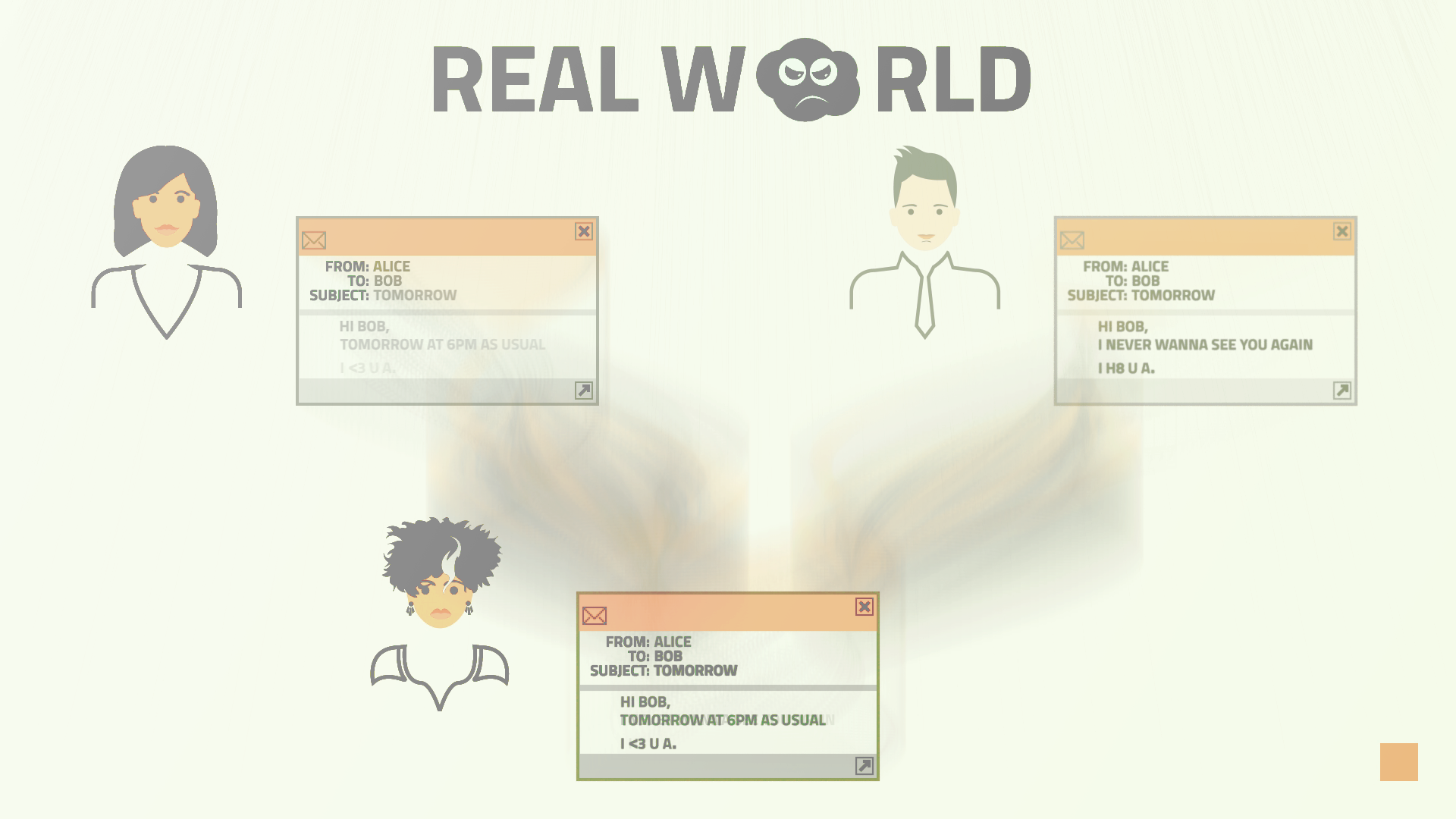
Picture 2: hazy shade over email communication in the real world. So without further ado, look at the Video 1 where the first episode of our email soap opera unveils the risks of unsecured email communication.
Video 1: Episode 1 - Email communication: casual communication. In the ideal world, everything works as expected. In the real world, evil forces reign.
This might have been an unpleasant surprise to all of you who like mathematics. But do not worry, when we cover the backstory, we will return to mathematics and - of course - to how it applies to the confidentiality, integrity and general security of email communication. But more on that next week. See ya!
References
-
https://trustica.cz/en/2018/01/11/internet-messaging-part-2/
-
https://trustica.cz/en/2018/01/18/internet-messaging-part-3/
-
Wikipedia contributors. (2018, May 19). Simple Mail Transfer Protocol. In Wikipedia, The Free Encyclopedia. Retrieved 20:31, May 23, 2018, from https://en.wikipedia.org/w/index.php?title=Simple_Mail_Transfer_Protocol&oldid=841925025
-
Wikipedia contributors. (2018, May 23). Transport Layer Security. In Wikipedia, The Free Encyclopedia. Retrieved 20:32, May 23, 2018, from https://en.wikipedia.org/w/index.php?title=Transport_Layer_Security&oldid=842607968
