Secure email communication
Written by Dominik Joe Pantůček on 2018-05-31
emailLast week we have discussed something rather boring - casual email communication and the security implications (or more like the lack of security) of using it. We have just re-phrased the well-known fact that casual email communication is far from secure with respect to confidentiality, integrity and authenticity. Today we are about to present a widely used class of solutions that make Eve's life harder, but I am afraid that today is not the day I can present you with ultimate solution to email communication security. But as you probably know, security is a gradual process rather than a product - a silver bullet - that solves all your problems. Read on for our gradual approach.
If you just wanna see the next part of our email soap opera - here it is.
In the first episode[1], we have talked about casual email communication. Alice wanted to send an email to her friend Bob and evil Eve wanted to interfere. Given the clear-text nature of email, it war relatively easy for her to capture the communication in question and even it was possible for her to inject fraudulent message between the two parties.
In this episode, we look at the scenario where Eve and Bob are using reasonably strong cryptography to protect their communication and identities. For encryption they can use the Elliptic Curve Diffie-Hellman (ECDH) key exchange[2]. For digital signature, typically a variant of Schnorr's signature[3] built on top of elliptic curves[4] would be used nowadays. So in an ideal secure world, although Eve can capture the data of the message mid-flight, there is nothing she can do about it. Except for reading email headers - such as the subject.
As you can see in Picture 1, it is easy to know that Alice is sending email to Bob and the subject of such email is "Tomorrow". But that about wraps it for Eve in a secure ideal world.
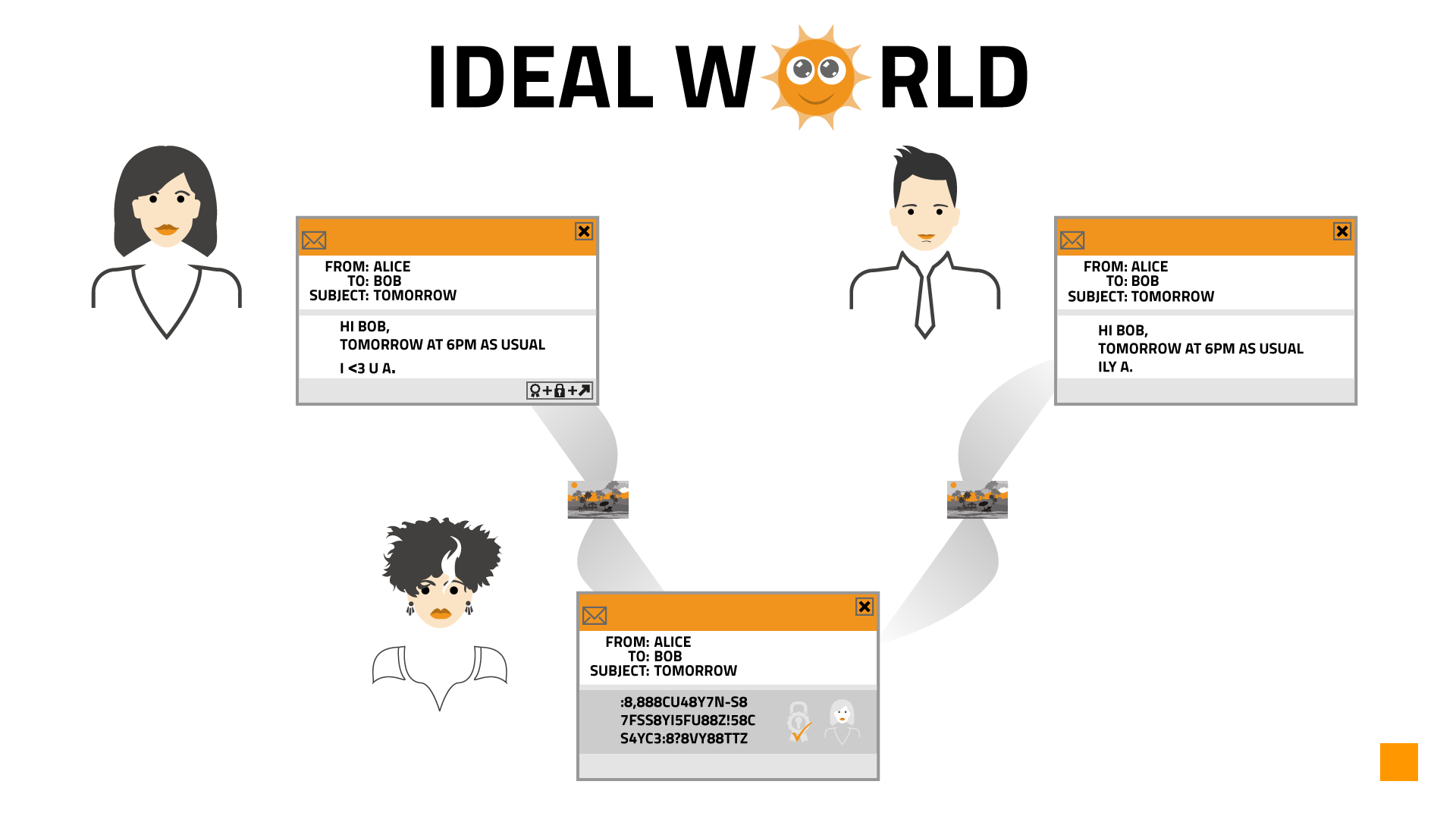
Picture 1: Secure communication in an ideal world. But - as you might have guessed - the world is not always ideal. There is malware, there are keyloggers and crackers[5] (not to be confused with hackers[6]) are just about everywhere. In the real version of secure world - or at least with general perception of security - it is hard and sometimes impossible to trust your personal computer. You might be using closed source operating system and applications - therefore you cannot tell what happens to your data. There might be bugs in the applications and which the evil forces know how to abuse... And of course there might be a lack of reasonable physical security in public places.
So with the multitude of cracking instruments in her hands, Eve compromises the security of Alice's computer and then she just waits on the line, captures the communication she wants to compromise, decrypts it easily and once again she is able to forge a fraudulent message pretending to be Alice. As you can see in Picture 2, losing your private keys means losing your digital identity.
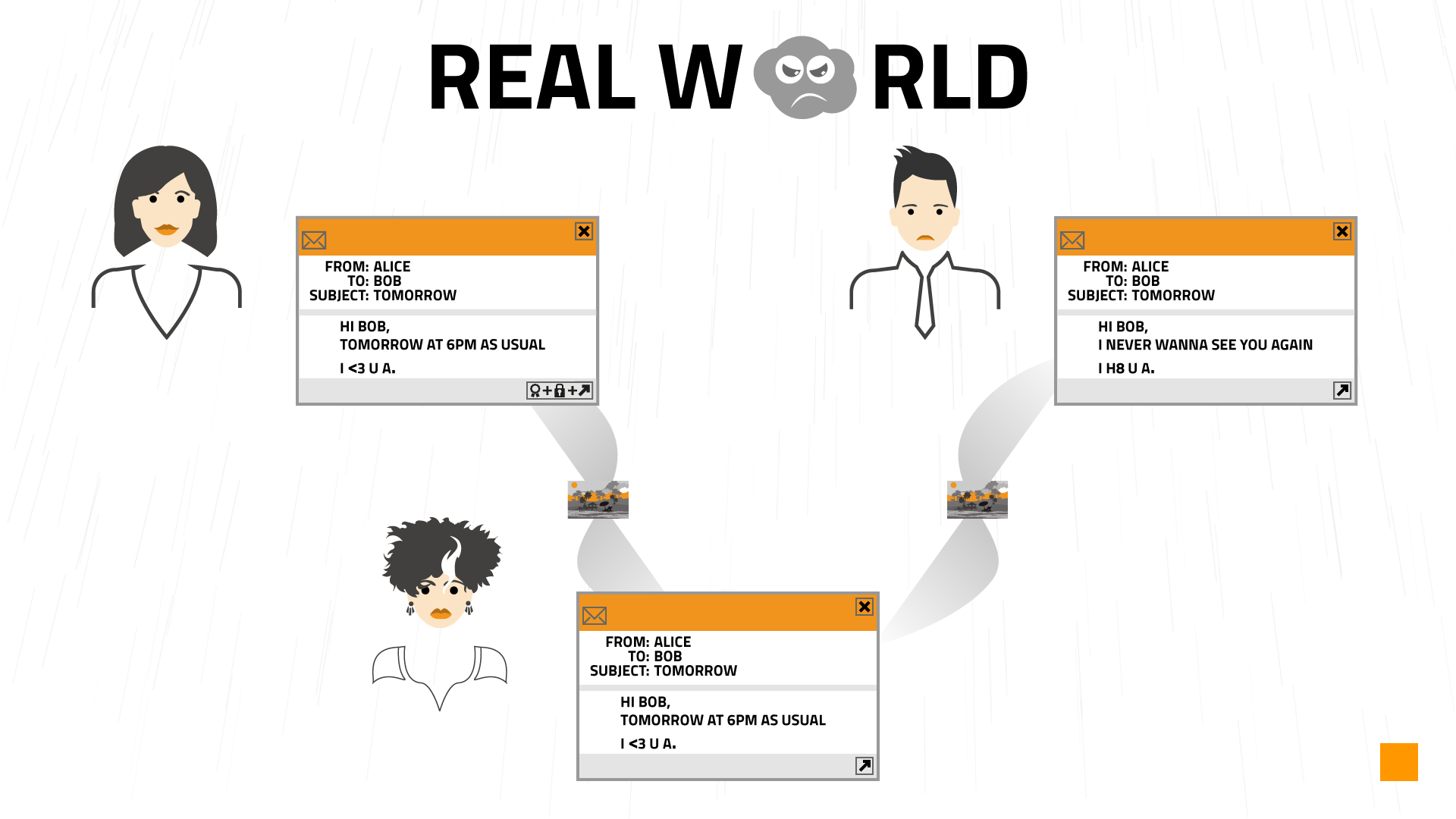
Picture 2: Secure communication in the real world. So without further ranting about what worse can happen to your communication, I can only suggest you have a look at Video 1 with the episode 2 of our email soap opera where the ciphers and attacks can be seen in nice action-packed format.
Video 1: Comparison of signed and encrypted email communication an an ideal world and in the real world.
Thank you for bearing with us so long and maybe next week we will present a possible solution to the problems presented today. See you next week!
References
-
https://trustica.cz/en/2018/05/24/casual-email-communication/
-
https://trustica.cz/en/2018/05/17/elliptic-curve-diffie-hellman-key-exchange/
-
Wikipedia contributors. (2018, January 30). Schnorr signature. In Wikipedia, The Free Encyclopedia. Retrieved 15:02, May 30, 2018, from https://en.wikipedia.org/w/index.php?title=Schnorr_signature&oldid=823175408
-
Wikipedia contributors. (2018, March 3). Elliptic Curve Digital Signature Algorithm. In Wikipedia, The Free Encyclopedia. Retrieved 15:02, May 30, 2018, from https://en.wikipedia.org/w/index.php?title=Elliptic_Curve_Digital_Signature_Algorithm&oldid=828648744
