Cryptoucan™ development: a look under the hood
Written by Dominik Joe Pantůček on 2018-06-21
cryptoucanFor those who have been wondering what is this Cryptoucan™ all about, wonder no more. We are ready for medium-scale batch production and you will be able to get your own Cryptoucan™ soon. Read on to find out how we designed the integrated circuitry.
Some of you may remember the Crypto Wars[1] of the 90's. And if you are among those who didn't notice back then, you are very lucky the cryptographers are still winning and there are not many countries in the developed parts of the world, where personal cryptography is illegal. But that is not enough. People should be in charge of their private data and strong cryptography at public hands means strong protection of privacy. And it is not just a strong cryptography you need to strongly protect the privacy, you also need a secure means of applying that cryptography.
For the past few decades, you could use the cryptographic software on your computer - but computers are easy to crack into. Basically you just need a screwdriver and some basic knowledge about how the computer operates. Other option were smart cards[2] which promise a strong protection of your private keys - yet sometimes it is hard to verify it is actually the case. Those cards also need a dedicated smart card reader which is another barrier to wide adoption. And also - for a smart card reader to be completely trusted, it must contain a PIN-pad and must not rely on a computer's keyboard.
To improve the way people handle their private keys, we put a really strong effort into designing a device that would combine the best of what smart cards might offer and what a convenient modern peripheral device employs. Imagine a device that would protect your private keys, you could just plug it in your computer and use it immediately and imagine no secret material (be it PIN or cryptographic key) ever leaves the device. Imagine Cryptoucan™.
Today, we would like to give you a slight hint into the process of the integrated circuitry and PCB[3] development. We had to work hard to protect the private keys, we had to resolve some engineering challenges as creating really small keyboard which does not leak any information via some side-channels and of course, we had to think about the overall design of the device. It is not "design first" in our case - we are "security first" kind of folks - but the design is important as we do understand that ease-of-use is necessary to improve security. In Video 1 you can see what we went through!
Video 1: Cryptoucan™ inception, development of integrated circuitry and PCB design for batch production. Looking at Picture 1, you can see the very first prototype of our Cryptoucan™. We used a development kit provided with the processor we chose and soldered a testing keyboard manually. Using this prototype, we verified if the proposed solution is feasible and it had turned out - it was.
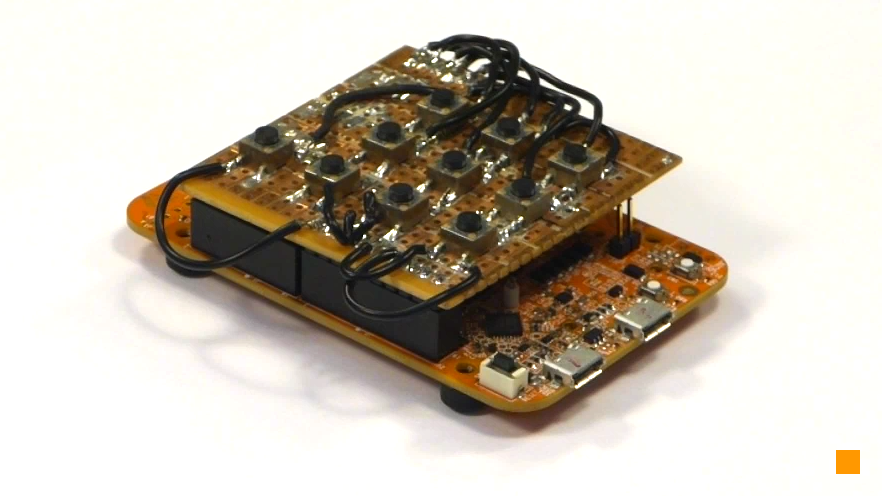
Picture 1: Very first prototype of Cryptoucan™ After verification of the basic concept, we went on to shrink the design a bit. Creating a touch keyboard that will be hard to eavesdrop and also it would be small enough to make the device fit easily in your pocket and on your keys - that turned out to be a very challenging task. You can see our keyboard tester in Picture 2. Yes, it is still slightly bulky, but we were able to measure all the required properties using this one.
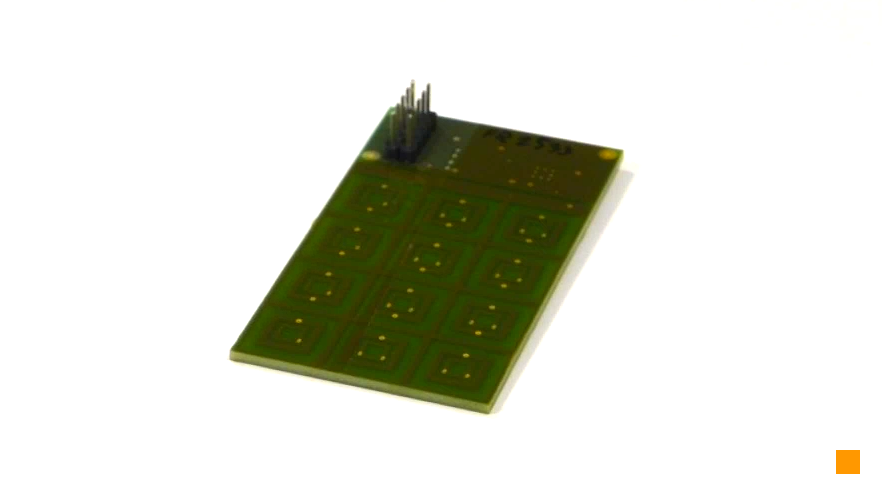
Picture 2: Keyboard tester which enabled us to measure how small the capacitors can be With keyboard parameters ready, we went back to the drawing board and designed the first integrated Cryptoucan™ prototype. The rectangular device in Picture 3 is exactly this intermediate step.
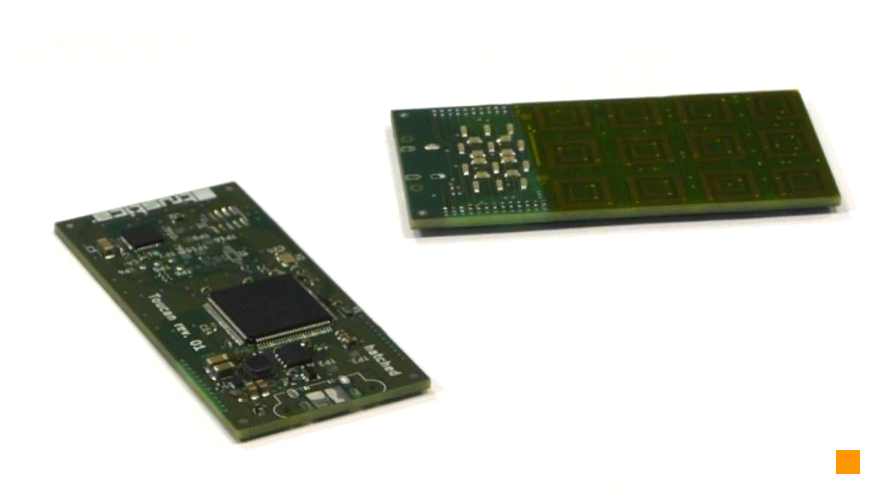
Picture 3: Cryptoucan™ PCB revision 1 - rectangular shape We tested the first revision thoroughly and as the design was working perfectly, we looked into how we could merge the 3D design of the device body with the integrated circuitry. As can be seen in Picture 4, the resulting PCB is quite futuristic even without any enclosure.
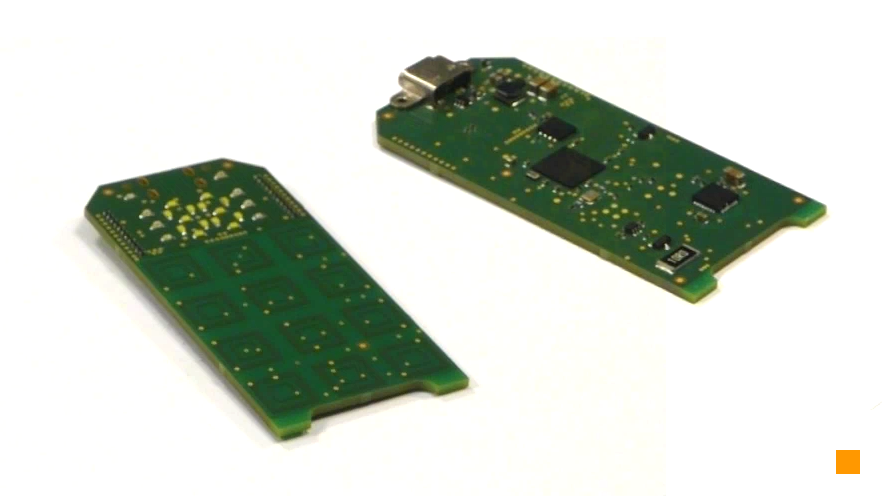
Picture 4: The futuristic design of Cryptoucan™ PCB revision 2 There is only one thing missing - isn't it? The elliptic curves[4] as the one in Picture 5 about which I have been ranting for quite some time. Not quite the same curve, but there are elliptic curve in Cryptoucan™ and they are the solid foundations on which the Cryptoucan's™ security is built.
Picture 5: Elliptic curve in simple Weierstrass form over a finite field
I can only hope you find the problem of protecting users' private keys as intriguing as we do. Remember to subscribe to our YouTube channel[5] and to follow us on Twitter[6] to find out more as we release more details about Cryptoucan™ communication[7]. See you next week!
References
-
Wikipedia contributors. (2018, April 27). Crypto Wars. In Wikipedia, The Free Encyclopedia. Retrieved 12:58, June 21, 2018, from https://en.wikipedia.org/w/index.php?title=Crypto_Wars&oldid=838549969
-
Wikipedia contributors. (2018, June 15). Smart card. In Wikipedia, The Free Encyclopedia. Retrieved 12:59, June 21, 2018, from https://en.wikipedia.org/w/index.php?title=Smart_card&oldid=846047233
-
Wikipedia contributors. (2018, June 7). Printed circuit board. In Wikipedia, The Free Encyclopedia. Retrieved 13:01, June 21, 2018, from https://en.wikipedia.org/w/index.php?title=Printed_circuit_board&oldid=844830954
-
https://trustica.cz/en/2018/06/14/toucan-email-communication/
