Cryptoucan™ usage: Initialization
Written by Dominik Joe Pantůček on 2018-07-26
cryptoucanThorough the last few months, we have shown you a lots of mathematical theory, we have tackled the problems of secure online communication and of data confidentiality and authenticity in general and we have revealed we are working on a device that should enable casual computer users to increase their overall data security with respect to all imaginable aspects. Read on to see one of our first prototypes securing the email communication.
Before you start using Cryptoucan™ for your day-to-day communication, you need to initialize it first. One of our goals was to ensure that nobody can read your private keys from the device. And if we want to talk about keeping the private keys private inside Cryptoucan™, it means they should never ever be anywhere else. That means the keys must be generated by Cryptoucan™ itself.
If you just want to see Cryptoucan™ being initialized in a video - here we go!
That said, initializing Cryptoucan™ means - mostly - generating the keys. Or more precisely private-public key pairs[1].
In our example, you can see Mozilla Thunderbird[2] email client with Enigmail[3] extension interacting with Cryptoucan™. From the main menu we went to the Enigmail submenu and selected the Key Management option as in Picture 1.
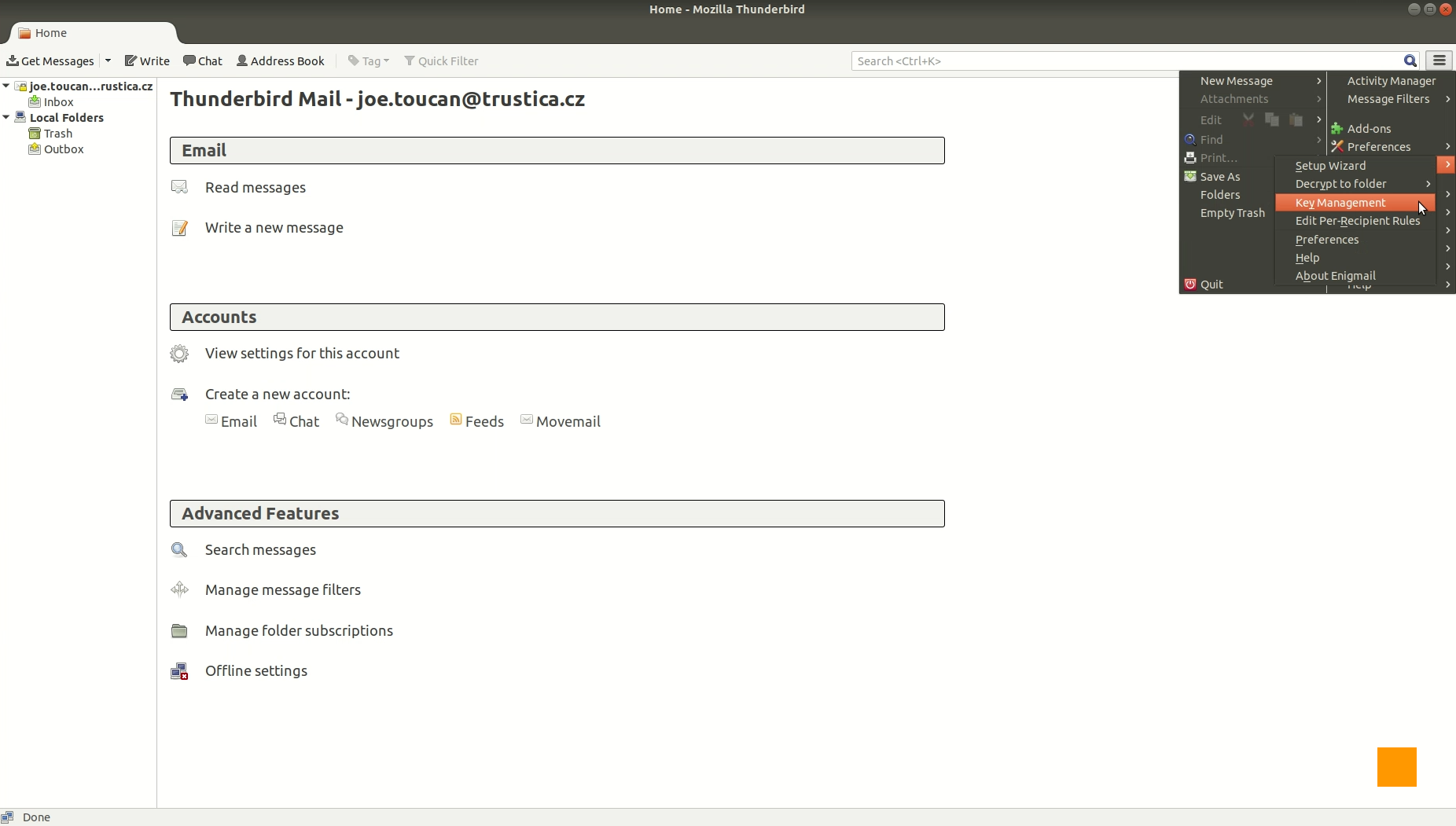
Picture 1:Mozilla Thunderbird's Enigmail main menu with Key Management option highlighted. This brings us to the Key Management window. Enigmail allows you to manage all your OpenPGP[4] keys here. But as our keys are to be stored inside Cryptoucan™, we choose to Manage SmartCard in the File menu as you can see in Picture 2.
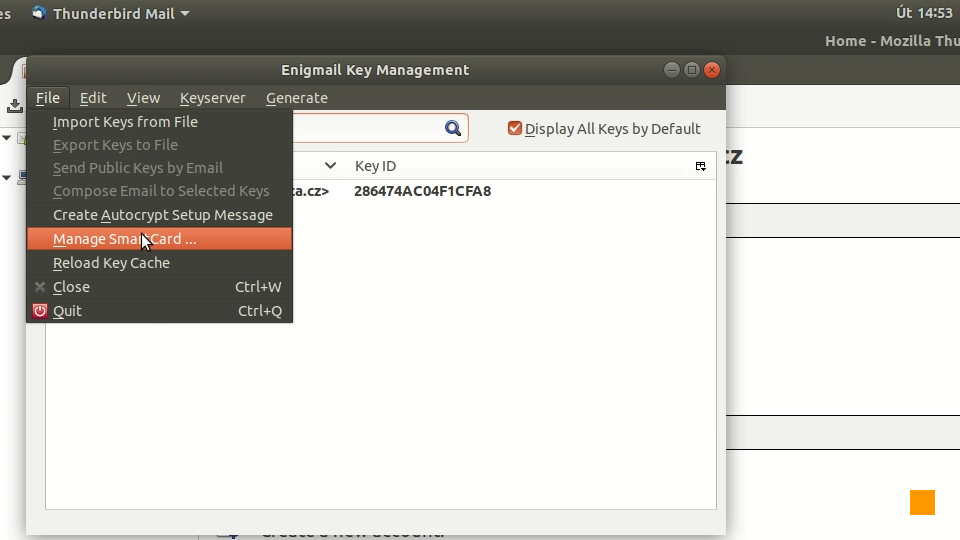
Picture 2: Enigmail's Key Management window showing the Manage SmartCard option in the File submenu. In the Card Management window, we can see the current information about the smart card. Why smart card you might ask. If you recall, this is the state-of-art way to handle public-key cryptography with securely stored private keys. Cryptoucan™ removes the pain of having to get a smart card reader and smart card. Generally speaking, it is a nicely wrapped smart card reader with PIN pad and programmed smart card permanently plugged in.
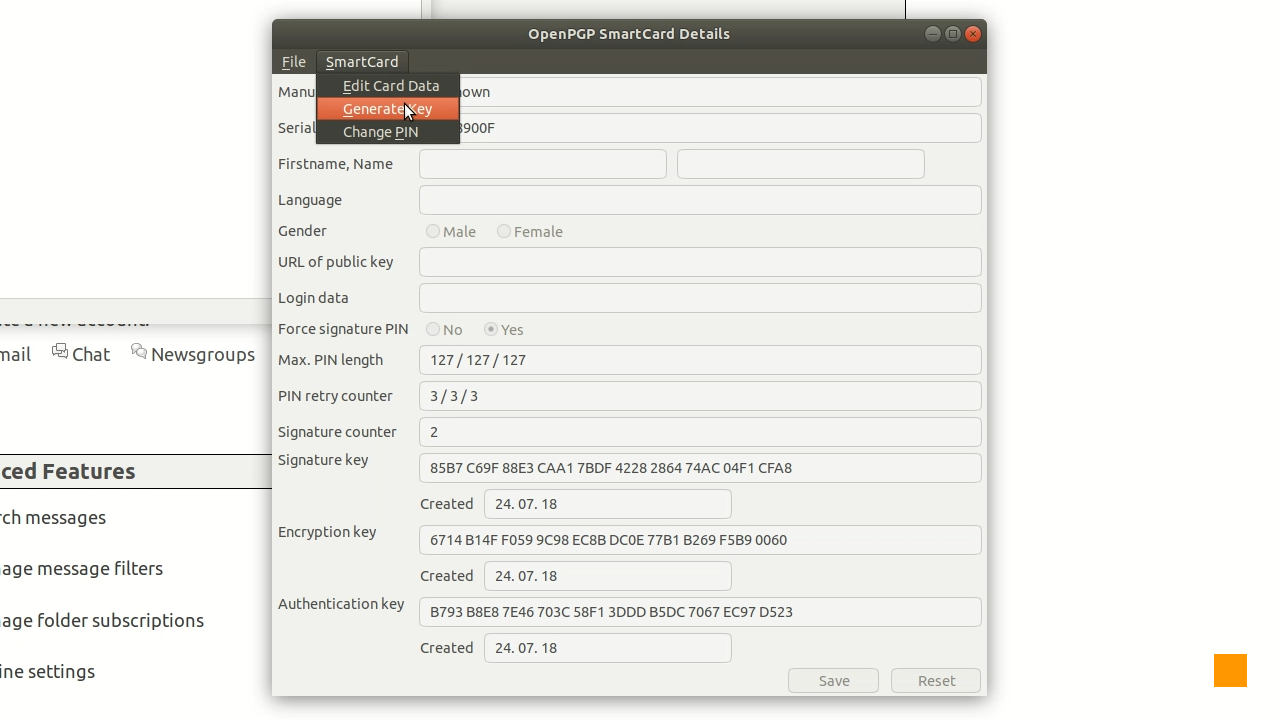
Picture 3: Enigmail's OpenPGP SmartCard Details window with Generate Key option of the SmartCard menu highlighted. There is not much information there right now in Picture 3 - but as you can see, there is information about the keys and some information about the card holder (we will discuss this later in this series). So we chose the Generate Key option in the SmartCard menu and that gives us the Generate OpenPGP key dialog - similar to the one seen in Picture 4.
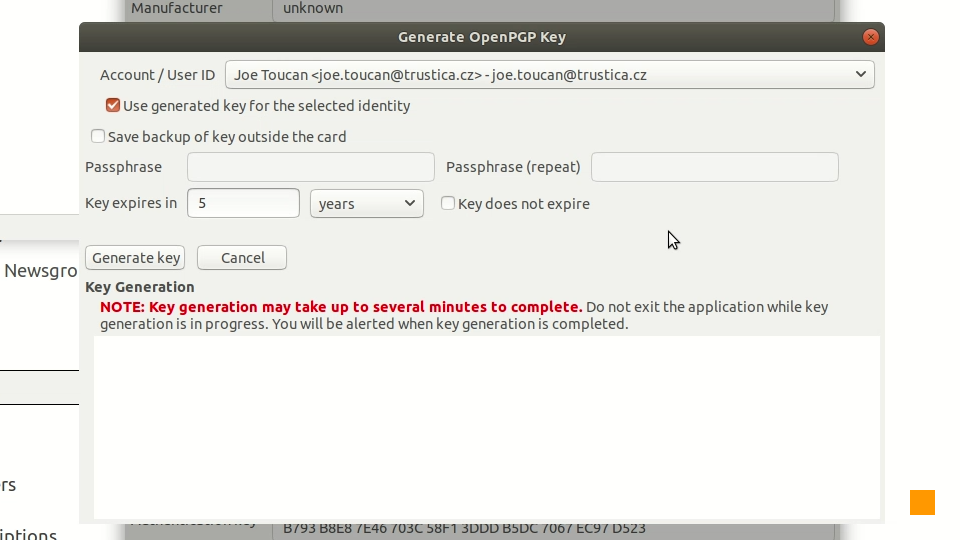
Picture 4: Generate OpenPGP Key dialog It is possible to adjust a few settings in this dialog. Mainly the identity for which the newly generated key should be used and also when should the key expire - if ever. But the most important setting is the option to save a backup of the newly generated key. This option must be turned off, because Cryptoucan™ is designed to keep the secret keys truly secret. Of course, generating the keys is just a matter of clicking on the Generate key button and then confirming it in the confirmation dialog depicted in Picture 5.
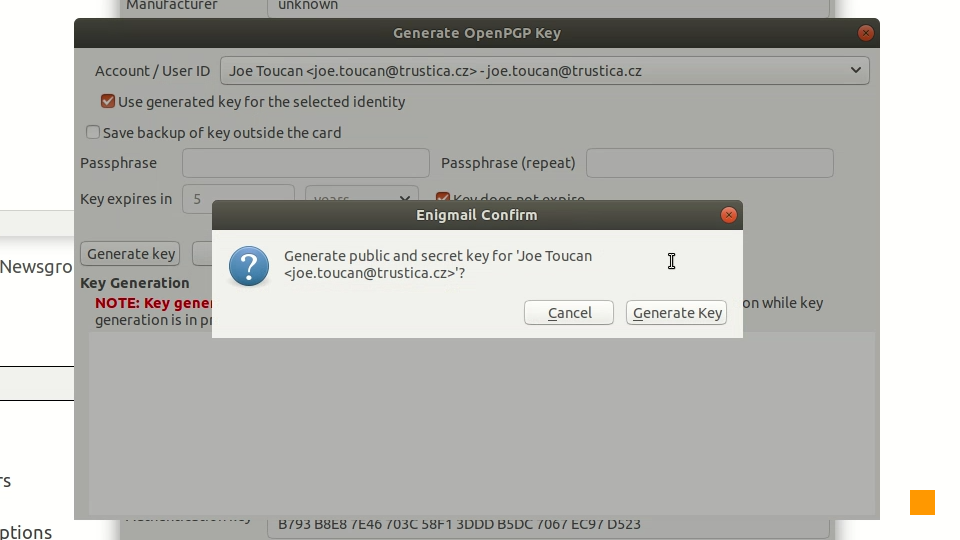
Picture 5: Enigmail confirmation dialog After confirming, the control is passed to Cryptoucan™ itself and you are prompted to unlock it - three times:
-
unlock with administrative PIN[5] number three (PIN3) to enable administrative access,
-
unlock with user PIN number one (PIN1) to start generating the keys,
-
unlock with user PIN1 once again to sign all the generated keys.
You might be wondering why such complexity. Personally, I could imagine using just the administrative PIN number three. But as we want Cryptoucan™ to be compatible with all current standards[6] and software that uses them, we have to follow current protocols and always double-check for possible compatibility issues. So yes, this procedure is required as any software communicating with Cryptoucan™ would first enable the administrative access (which requires to to enter PIN3) and then use PIN1 authorization to start the process. And then again PIN1 authorization for signing the newly generated keys.
To make things even funnier, Cryptoucan™ is basically required to stay unlocked after this operation, so we actively recommend to unplug it and plug it back into a USB[7] port of your computer. This way you ensure the secret material is not kept unencrypted in the device memory.
You might also wonder why signing. But remember, Cryptoucan™ provides you with three keys:
-
signing key,
-
encryption key,
-
authentication key
And all the keys are signed by the first one - which becomes self-signed. This is needed to ensure that you can publish the information that you own the respective private keys.
Now you have all the information about Cryptoucan™ initialization and how generate the key pairs with the device. You can see the whole process using Mozilla Thunderbird and Enigmail in the Video 1 below.
Video 1: Cryptoucan™ usage: Initialization Although the explanation was a bit lengthy, it is possible to safely assume that virtually anyone capable of using a computer is also capable to use Cryptoucan™ without further ado.
Thank you for keeping with us and if you are not subscribed to our YouTube channel[8] yet, subscribe now to always get the latest Cryptoucan™ news. And of course, you can follow us on Twitter[9] as well to stay in tough. See you next week with more information about Cryptoucan™ setup!
References
- Wikipedia contributors. (2018, July 20). Public-key cryptography. In Wikipedia, The Free Encyclopedia. Retrieved 17:10, July 25, 2018, from https://en.wikipedia.org/w/index.php?title=Public-key_cryptography&oldid=851218348
2.Mozilla Thunderbird, available online at https://www.thunderbird.net/
3.Enigmail: A simple interface for OpenPGP email security, available online at https://enigmail.net/
-
OpenPGP: Email encryption. For all operating systems. Standing the test of time. Available online at https://www.openpgp.org/
-
Wikipedia contributors. (2018, July 22). Personal identification number. In Wikipedia, The Free Encyclopedia. Retrieved 17:13, July 25, 2018, from https://en.wikipedia.org/w/index.php?title=Personal_identification_number&oldid=851423929
-
Wikipedia contributors. (2018, June 10). PC/SC. In Wikipedia, The Free Encyclopedia. Retrieved 17:13, July 25, 2018, from https://en.wikipedia.org/w/index.php?title=PC/SC&oldid=845286036
-
Wikipedia contributors. (2018, July 19). USB. In Wikipedia, The Free Encyclopedia. Retrieved 17:14, July 25, 2018, from https://en.wikipedia.org/w/index.php?title=USB&oldid=851034765
.8. Trustica channel, available online at https://www.youtube.com/channel/UC-RuV9nXyysbH0kB4pVqZTg
.9. Trustica Twitter, available online at https://twitter.com/trusticacz
