Cryptoucan™ usage: SSH authentication
Written by Dominik Joe Pantůček on 2018-09-06
cryptoucanWith the maintenance release of GnuPG and finalizing our manufacturing process before starting another small batch production this week, the last week was without an associated video. Read on to see one that will show you some functionality beyond casual email signing and learn why we are so excited that Cryptoucan™ is nearing retail release!
With Cryptoucan™ ready for release[1], we want to show you more features than just how to set it up[2][3][4] and how to sign emails[5]. Today we will talk about SSH public key authentication. Secure Shell protocol - SSH[6] - allows the users to connect to remote systems over encrypted channel and work in an command-line environment like on a local computer. There are many options for authenticating SSH sessions: passwords, public-key cryptography, one-time passwords or you can for example use Kerberos[7] tickets for single sign-on solution.
If you just want to see the video about using Cryptoucan™ for authenticating SSH sesions: here you go.
But maybe this time I would suggest to read the article anyway. Using Cryptoucan™ for SSH authentication is simple and elegant solution as it overcomes the need to use and transfer passwords - which can be sniffed from the keyboard by malicious software. It also ensures that the private keys used for authentication are never touched by the computer you are using and therefore even if your computer gets compromised, the malicious software cannot steal them!
You can see an overview of Cryptoucan™ SSH authentication in Picture 1 below. The process starts by connecting to the SSH server which gives you a cryptographic challenge to sign. The signing (authentication) key is stored in your Cryptoucan™ and so your SSH client passes this challenge on to it and Cryptoucan™ creates the requested signature.
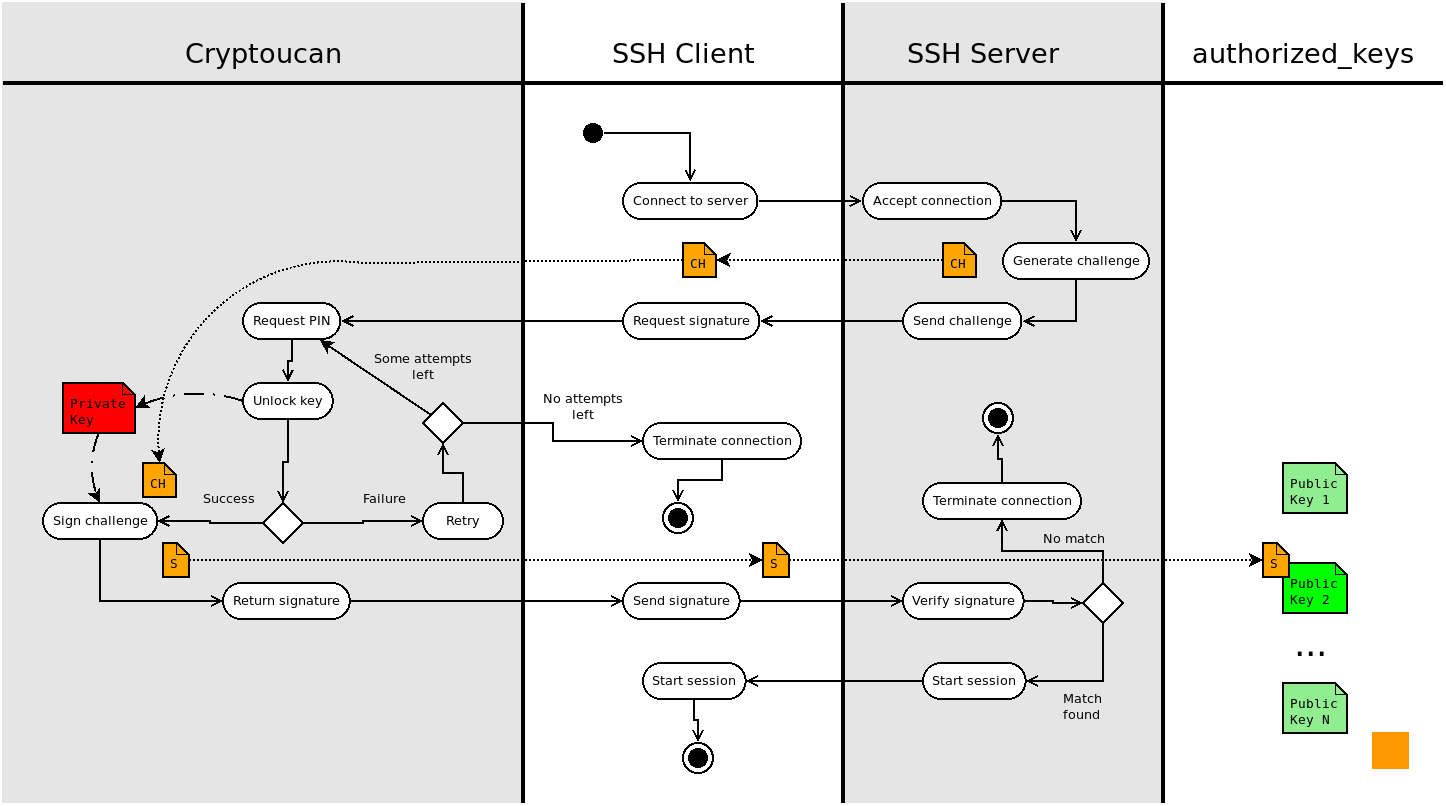
Picture 1: Swim-lanes flowchart of SSH authentication with Cryptoucan™ This is neat - as signing the challenge with Cryptoucan™ requires you only to enter the user PIN1 on the device and the rest "just happens". Cryptoucan™ gives the signature back to SSH client which in turn sends it to the server. The server then matches the signature against known list of authorized keys and if it finds a match, you are authenticated and your SSH session starts immediately.
You can see the explanation and Cryptoucan™ in action in Video 1 below.
Video 1: SSH authentication with Cryptoucan™ explained and shown
I hope this feature shows off that OpenPGP[8] is not only about signing and encrypting emails. It is also about user authentication. And there is also much more to see: key management, software signing, web of trust, key revocation... you name it. See you next week with more!
References
-
https://trustica.cz/2018/08/09/cryptoucan-usage-personal-information/
-
https://trustica.cz/2018/08/02/cryptoucan-usage-pin-management/
-
https://trustica.cz/2018/07/26/cryptoucan-usage-initialization/
-
https://trustica.cz/2018/08/16/cryptoucan-usage-signing-emails/
-
Wikipedia contributors. (2018, August 10). Secure Shell. In Wikipedia, The Free Encyclopedia. Retrieved 20:56, September 5, 2018, from https://en.wikipedia.org/w/index.php?title=Secure_Shell&oldid=854340922
-
Wikipedia contributors. (2018, June 12). Kerberos (protocol). In Wikipedia, The Free Encyclopedia. Retrieved 20:59, September 5, 2018, from https://en.wikipedia.org/w/index.php?title=Kerberos_(protocol)&oldid=845591269
-
OpenPGP: Email encryption. For all operating systems. Standing the test of time.; homepage available online at https://www.openpgp.org/
