Key management - introduction
Written by Dominik Joe Pantůček on 2018-09-13
cryptoucanAlthough there are things moving quickly ahead with Cryptoucan™, we will slow down with our publishing schedule and look at related - and very important - topic. Having trusted and secure cryptographic token is just one part of the puzzle. Read on to get some tips for various scenarios where you need more than just a key which you can use for signing or decrypting something.
We have already discussed[1] possibilities of securing email communication. These possibilities extend also to other areas of interest. It does not matter what do you want to sign or encrypt, the principle is the same. You always use your private key for signing data and decrypting what others encrypted for you. And similarly, others use your public key to verify your signatures and encrypt data for you. It is nicely covered in my song[2][3] which you can watch online.
The problem we have not tackled yet is how to distribute your keys to your peers and how to get theirs. The simplest way to do it is just to send them via email. Yet - as you are initially using unsecured email - you must verify the integrity of the keys sent and received. As you can see in Picture 1, you should use another communication channel to verify the fingerprint of the key. A fingerprint of your key is typically a hash[4] of the main public key (used for signing) you send someone (or receive from someone). And the other keys - for encryption and authentication - can be signed by the signing key. It means there is only 1 fingerprint you need to verify.
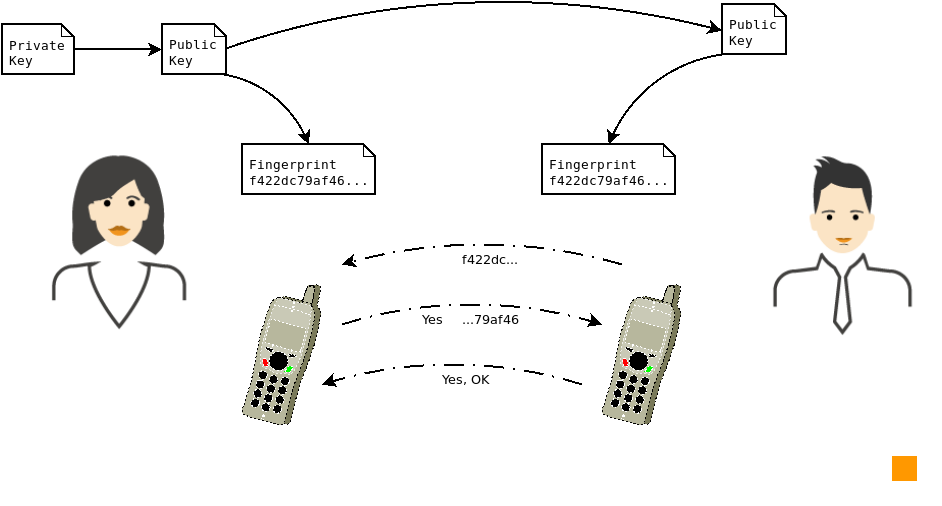
Picture 1:Alice sending Bob her public key, afterwards they verify the fingerprint over the phone. Of course, it would be the best to verify the fingerprint in person. But honestly - a phone call is also good, if you already know the other person's voice.
But now ask yourself what happens if you lose your private key? Or worse - what if someone steals it?
In both cases, you must create a new key - actually all of the keys in question. And in the latter case you should publish your revocation certificate. You probably remember that we skipped generating revocation certificate in the initialization[5] description and yes, in real world, you should always have your revocation certificate ready in case your keys get compromised!
The problem is that now (with a new key) you have to - once again - ensure, it is distributed and everyone gets it and verifies its integrity. So the question is, how do you prove it is your key without going through the lengthy verification using different channel?
Consider the following scenario. You generate your keys, distribute the public key used for signing and ensure everyone has verified its integrity by checking the fingerprint over another communication channel. Now you generate another set of keys and sign it with the first signing key. Then you put the first signing private key in a cold storage - for example lock it in a safe. The second set of keys you can use normally and everyone can see, that they are yours. Of course, if you need to create new keys, you just generate them and once again, signing them with the first key ensures their authenticity.
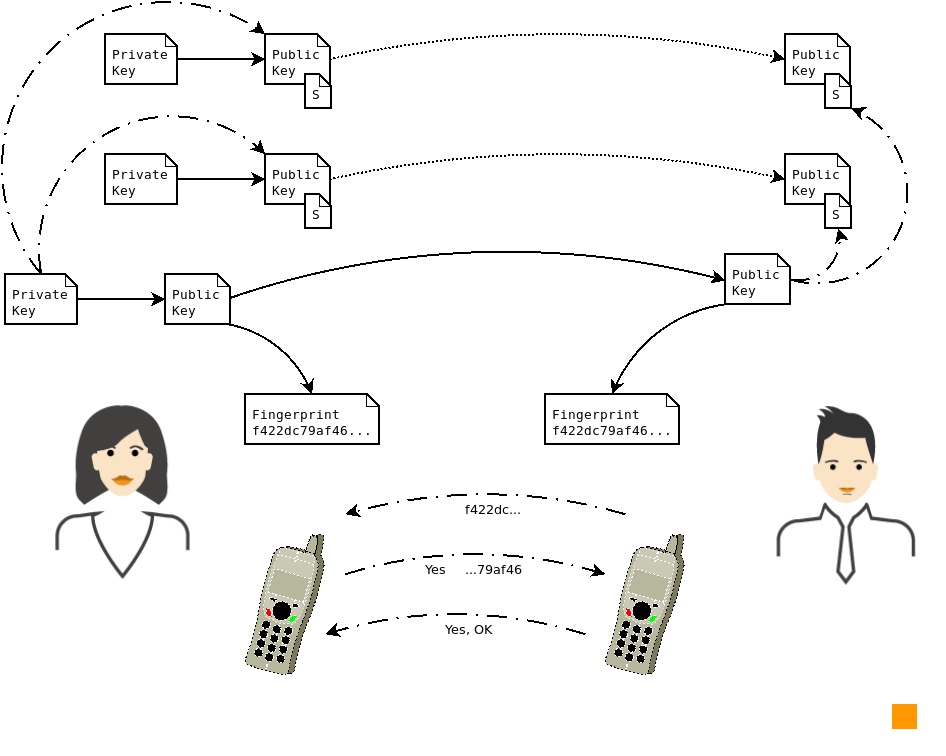
Picture 3:Alice sending Bob her master public key and afterwards they verify its fingerprint. Other keys are then signed by this master key and can be distributed without further verification. The first key is called a master key and you can see such setup in Picture 3 above. Following this procedure allows you to change your casual keys regularly - for example once a year - and therefore it improves the overall security of how you use your cryptographic keys.
And even though this setup does not cover all scenarios that may happen, for ensuring the authenticity of your keys and allowing their easy rotation, it is more than enough. If you want to ensure the availability of your encrypted data even in the situation where you lose some of your keys, the setup is slightly more complex - and we will definitely look into it in the future.
Thank you for reading our series and rest assured, There is more to come! Come back next week for more Cryptoucan™ news.
References
-
https://trustica.cz/en/2018/08/30/securing-email/
-
Wikipedia contributors. (2018, September 11). Hash function. In Wikipedia, The Free Encyclopedia. Retrieved 19:41, September 13, 2018, from https://en.wikipedia.org/w/index.php?title=Hash_function&oldid=859079016
-
https://trustica.cz/en/2018/07/26/cryptoucan-usage-initialization/
