Cryptoucan™ cryptographic model
Written by Dominik Joe Pantůček on 2018-12-20
cryptoucanCreating a truly secure cryptographic storage requires thinking hard about the cryptographic model for protecting the secret keys. Read on to see the approach we have designed and implemented.
Securing cryptographic tokens with PIN[1] cannot be seen as simple comparison between what the user enters and what is stored in some memory on the device. That is extremely dangerous. Should the attacker gain access to the on-device memory, he can simply read the PIN that is written there. Although such attacks require quite some effort and very expensive equipment, they surely are feasible to state-level adversary.
Thinking about this problem, you quickly realize that it is not just the secrecy of the PIN you need to assure. You need to protect the secret keys as well. And considering the possibility of attacker somehow reading the memory contents, it brings us to rather simple solution: what if we encrypt all the secret keys using a PIN-derived symmetric key[2].
But how to do this if there are multiple PINs in use? That is not so straightforward but with the help of intermediate key - which actually acts as a symmetric master key - it is possible. The generic idea is outlined in Picture 1 below.
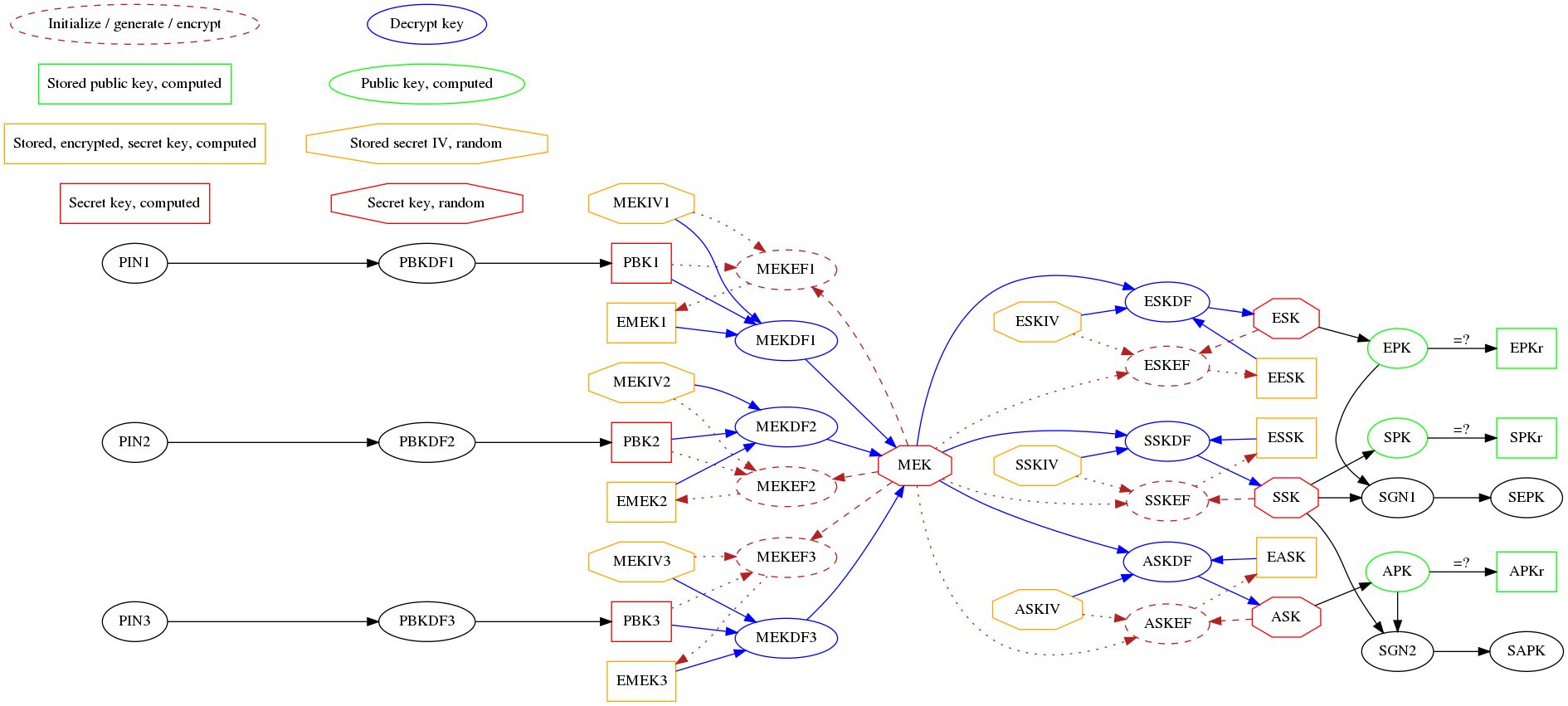
Picture 1: simplified diagram of the cryptographic scheme Do not focus on actual abbreviations in given picture, but rather think about the general approach here. The master key is encrypted three times - each time with different PIN-based key as encryption key. This way, it is possible to decrypt the master key using any of the three PINs. Of course, in order to change any PIN, you need to re-encrypt the master key for given PIN-based key.
We can think about it in terms of cryptographic functions:
-
- function that takes key and initialization vector and encrypts clear-text message to cipher text
-
- function that decrypts cipher text using given key and initialization vector to clear-text message
-
- master encryption key
-
- function that computes PIN-based key from given
Now for PIN1 we get: Where is initialization vector used with PIN1 and is the master encryption key encrypted with PIN1-derived key. During initialization, is filled with random bits and then is computed as follows: And of course, with master key unlocked, it is possible to continue down the chain and unlock one of the asymmetric keys[3] - for example the secret signing key like: Where is - of course - the initialization vector used for encrypting .
With this beautiful scheme, it is possible to verify, whether the user entered the correct PIN and during this process, actually (mathematically) unlock the secret keys the token uses.
Thank you for following Cryptoucan™ development for so long and enjoy the winter solstice[4] tomorrow!
References
-
Wikipedia contributors. (2018, November 21). Personal identification number. In Wikipedia, The Free Encyclopedia. Retrieved 20:41, December 19, 2018, from https://en.wikipedia.org/w/index.php?title=Personal_identification_number&oldid=870001317
-
Wikipedia contributors. (2018, September 5). Key derivation function. In Wikipedia, The Free Encyclopedia. Retrieved 20:41, December 19, 2018, from https://en.wikipedia.org/w/index.php?title=Key_derivation_function&oldid=858212346
-
Wikipedia contributors. (2018, December 8). Public-key cryptography. In Wikipedia, The Free Encyclopedia. Retrieved 20:42, December 19, 2018, from https://en.wikipedia.org/w/index.php?title=Public-key_cryptography&oldid=872600572
-
Wikipedia contributors. (2018, December 17). Winter solstice. In Wikipedia, The Free Encyclopedia. Retrieved 20:42, December 19, 2018, from https://en.wikipedia.org/w/index.php?title=Winter_solstice&oldid=874218414
