Side channel attacks: Display
Written by Jiří Keresteš on 2019-04-18
cryptoucanIn today's post, we will focus on one of Cryptoucan's many lines of defense: display power analysis attack prevention.
You may have noticed that side channel attacks are quite popular now. Vulnerabilities like Spectre[1], TLBleed[2], Foreshadow[3], or Rowhammer[4] (my personal favourite) show us that both hardware and software security are equally important. Exploiting hardware weaknesses does not necessarily require expensive lab equipment. Sure, there are many fancy attacks involving optical emission analysis or acoustic fault injection[5], but you can have fun with minimal equipment.
We are going to attack Cryptoucan using a very basic power analysis[6]. Cryptoucan has a two-digit segmented LED display. Each lit LED draws a few milliamperes of current. If we can somehow measure this current, we can monitor active LED count. Do this during the PIN entry operation and we have the number of PIN digits. Or do we? Let's try it out. Demo time!
You can see our USB current meter in the Picture 1. Although it might look complicated, it is just a shunt resistor on Vcc line, amplifier, and some connectors. Basically a current to voltage converter.
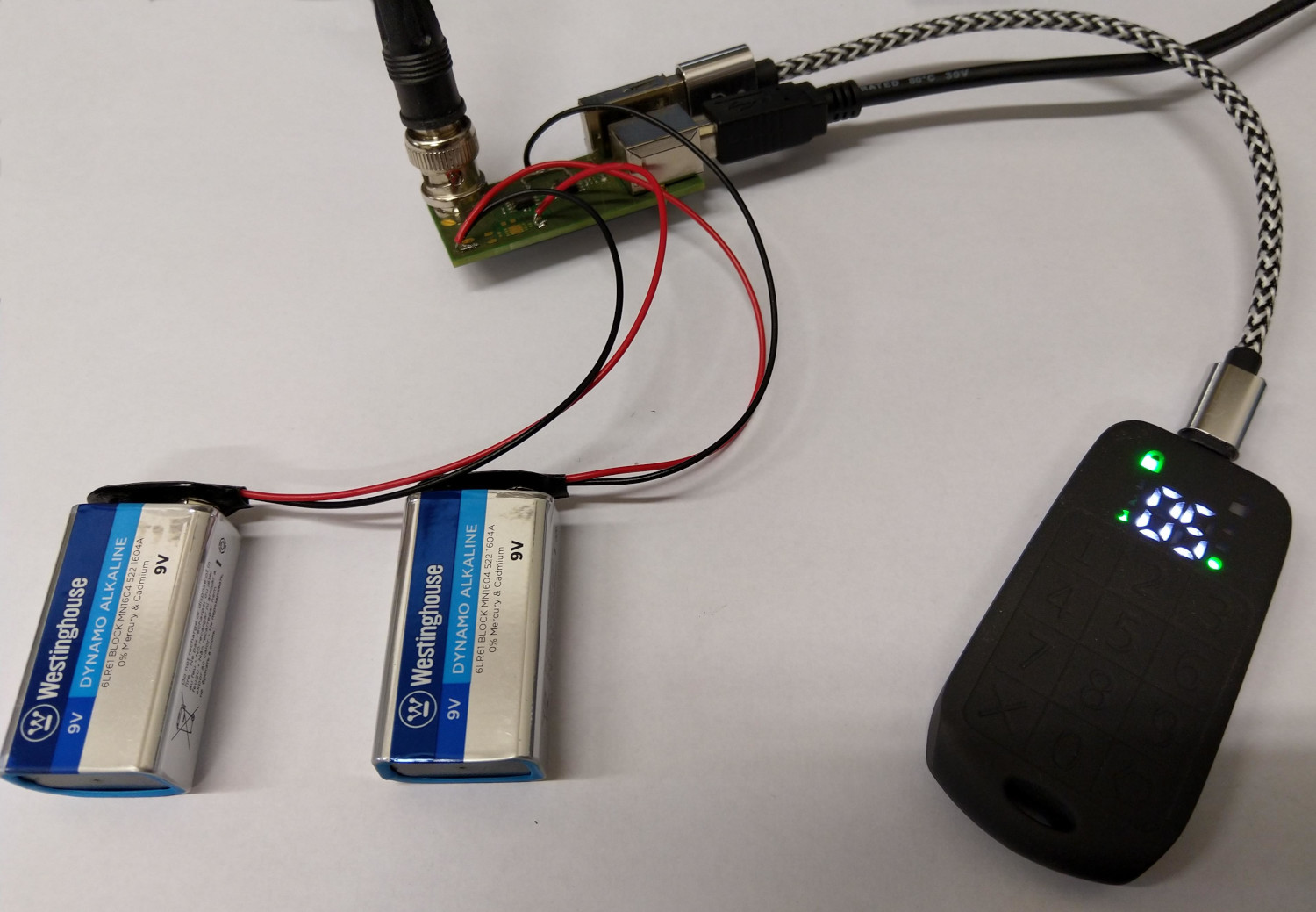
Connect it to an oscilloscope and you get some power traces. There will be quite a lot of noise from the Cryptoucan's internal power supply, so it will not be usable for any advanced power analysis. But our display draws rather large current and therefore it is fine for our purpose. We expect our trace to look like a trace in the Picture 2.
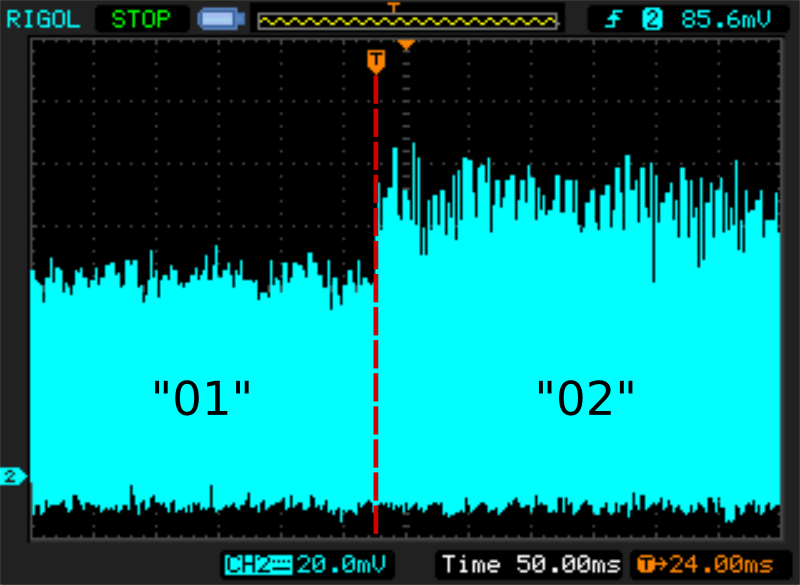
This is a power trace we get from a naive display implementation. We can clearly see the transition between numbers "01" and "02" shown on the display. However, Cryptoucan has a built-in countermeasure against this attack.
Power trace from our real implementation is in the Picture 3. Our internal protection module acts like a current buffer. It detects the number of active LEDs and adjusts its programmable load to keep the current constant. Furthermore, it adds some random decoy peaks to make analysis even harder.
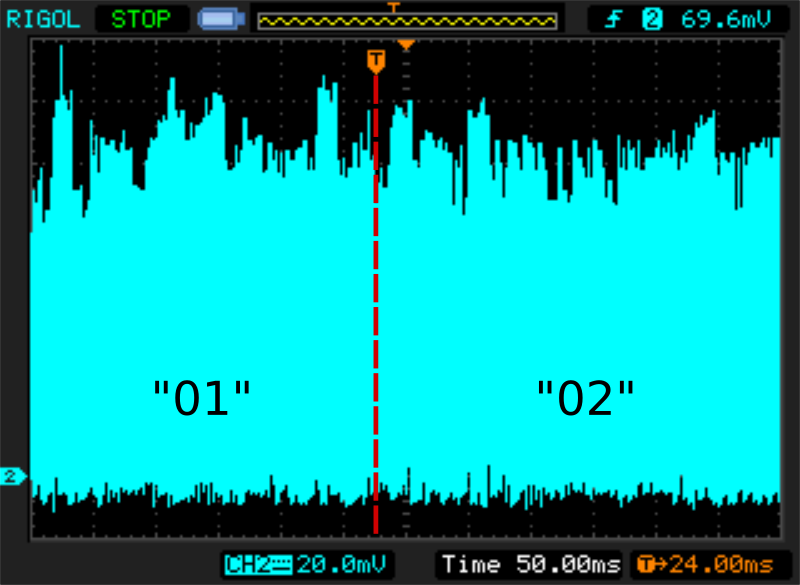
Let's sum it up. Cryptoucan is protected against this kind of attack, but there are many other tokens with OLED display, that might be vulnerable. Attacker does not even need to have a physical access to the device. Modern laptops sometimes have the ability to measure USB current, making it much easier for the attacker.
And that's all for today. Thanks for being with us and see you next Thursday!
References
- https://spectreattack.com/
- B. Gras, K. Razavi, H. Bos, C. Giuffrida, Translation Leak-aside Buffer: Defeating Cache Side-channel Protections with TLB Attacks, in: USENIX Security, 2018. https://www.vusec.net/download/?t=papers/tlbleed_sec18.pdf.
- https://foreshadowattack.eu/
- Y. Kim, R. Daly, J. Kim, C. Fallin, J. H. Lee, D. Lee, C. Wilkerson, K. Lai, O. Mutlu, Flipping Bits in Memory Without Accessing Them: An Experimental Study of DRAM Disturbance Errors. 2014 ACM/IEEE 41st International Symposium on Computer Architecture (ISCA). doi:10.1109/ISCA.2014.6853210
- Shahrad, M., Mosenia, A., Song, L., Chiang, M., Wentzlaff, D., & Mittal, P. (2018). Acoustic Denial of Service Attacks on Hard Disk Drives. Proceedings of the 2018 Workshop on Attacks and Solutions in Hardware Security - ASHES 18. doi:10.1145/3266444.3266448
- Wikipedia contributors. (2019, February 6). Power analysis. In Wikipedia, The Free Encyclopedia. Retrieved 12:48, April 16, 2019, from https://en.wikipedia.org/w/index.php?title=Power_analysis&oldid=882002219
