Cryptoucan™ usage: Key management on Windows
Written by Lída Hrnčířová on 2019-06-06
cryptoucanIn this blog post you'll learn how to manage your keys using Kleopatra Key Manager on Windows. We will show you basic operations such as importing and exporting keys, and certifying them. As usual, this is accompanied by instructional video showing you all the process.
You've already personalized your Cryptoucan™ and got your own set of keys. Now it's time to finally show you how to import other users' keys, how to certify them and how to export your keys.
If you came just to see the instructional video, click here!
Exporting keys
You're going to use this function if you ever want people to send you encrypted e-mails. This will export your public key, which you can then put to your personal webpage, upload to a key server, or just send to people. Whenever someone's going to send you an encrypted e-mail, they'll use this exported key, and you'll decrypt the message with your private key.
Once you open Kleopatra, you're going to see your key in the list right away.
-
Click the key you want to export, so it's highlighted, and then choose the option Export... at the top.
-
Kleopatra will ask you to choose the destination where you want to save the key.
-
When you click Save, the operation is done and exported key is ready to use.
Picture 1: Exporting key
Importing keys
Whenever you'd like to send an encrypted e-mail to someone, you'll need to use their public key. It's a good idea to build a library of keys to make encrypting an easy, quick process.
First of all, you'll need to download the key from trusted source. Then follow these steps:
-
Click* Import...* option in Kleopatra
-
Select the key file
-
Proceed with Open
Kleopatra will immediately ask you whether you want to certify the key you've just imported. We're going to explain this in the next paragraph. If you just want to import the key, click no and the process is done.
Picture 2: Do you want to certify the key?
Certifying imported keys
By certifying the keys you've imported, you're making sure the key really belongs to the person it's supposed to. This is done by comparing fingerprints. Fingerprint is a kind of checksum which is statistically unique to each key.
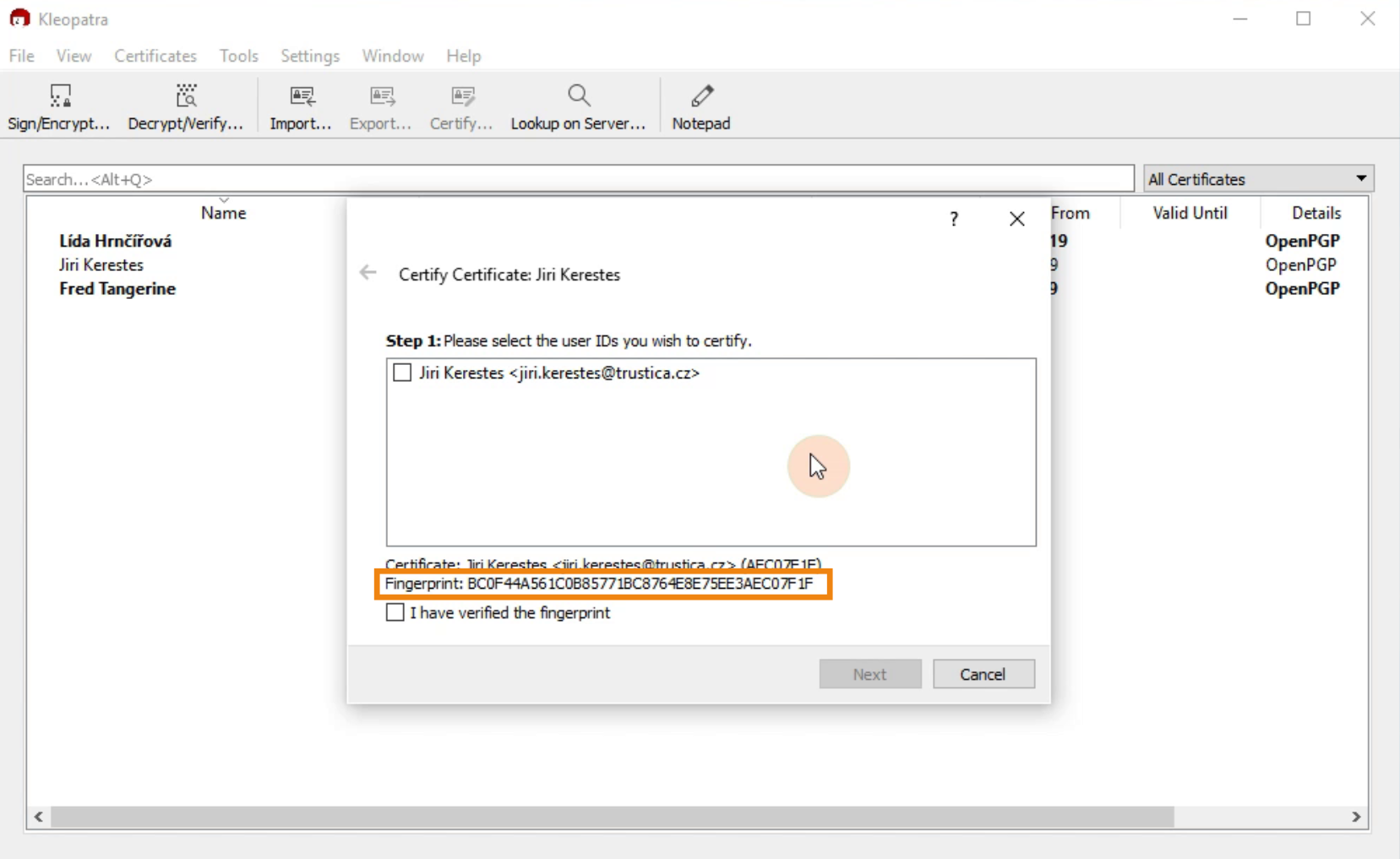
Picture 3: Fingerprint To check the fingerprint of the key you've imported, you'll have to retrieve the key fingerprint from the key owner via a trusted channel. Some examples are:
-
Messaging or calling the person.
-
Getting it from their trusted website.
You're going to need Cryptoucan™ to finish this process, as you are signing the key with your own certificate.
To certify the key:
-
Click Yes when Kleopatra asks you if you want to certify the key, or select the key in the list and then choose Certify... at the top.
-
This will open new window. You can see the fingerprint at the bottom of it. Compare the fingerprint with the one you got from your trusted source.
-
If it matches, check the box next to the identity of the key.
-
Also check the "I have verified the fingerprint" box.
-
Proceed with Next.
-
If you have multiple accounts with certificates, choose the one you want to certify the key with.
-
Choose whether you want to certify the key for you only or for everyone to see. If you choose the latter one and then upload it to a key server, users will see the key is already certified by someone else and can be trusted.
-
Click Certify.
-
Kleopatra will ask you to enter user PIN 1 on Cryptoucan's keypad, confirm it by pressing the hexagon symbol at the bottom right corner.
-
Once you've successfully entered the PIN, the process is done.
-
Press the Finish button.
Picture 4: Signing the key with Cryptoucan™
Checking the fingerprint without certification
If you just want to see the certificate fingerprint, you can do that too.
-
Double-click the imported key.
-
Compare the fingerprint you've got from your trusted source with the fingerprint at the bottom of the window that just opened.
You can also see other information about the key here.
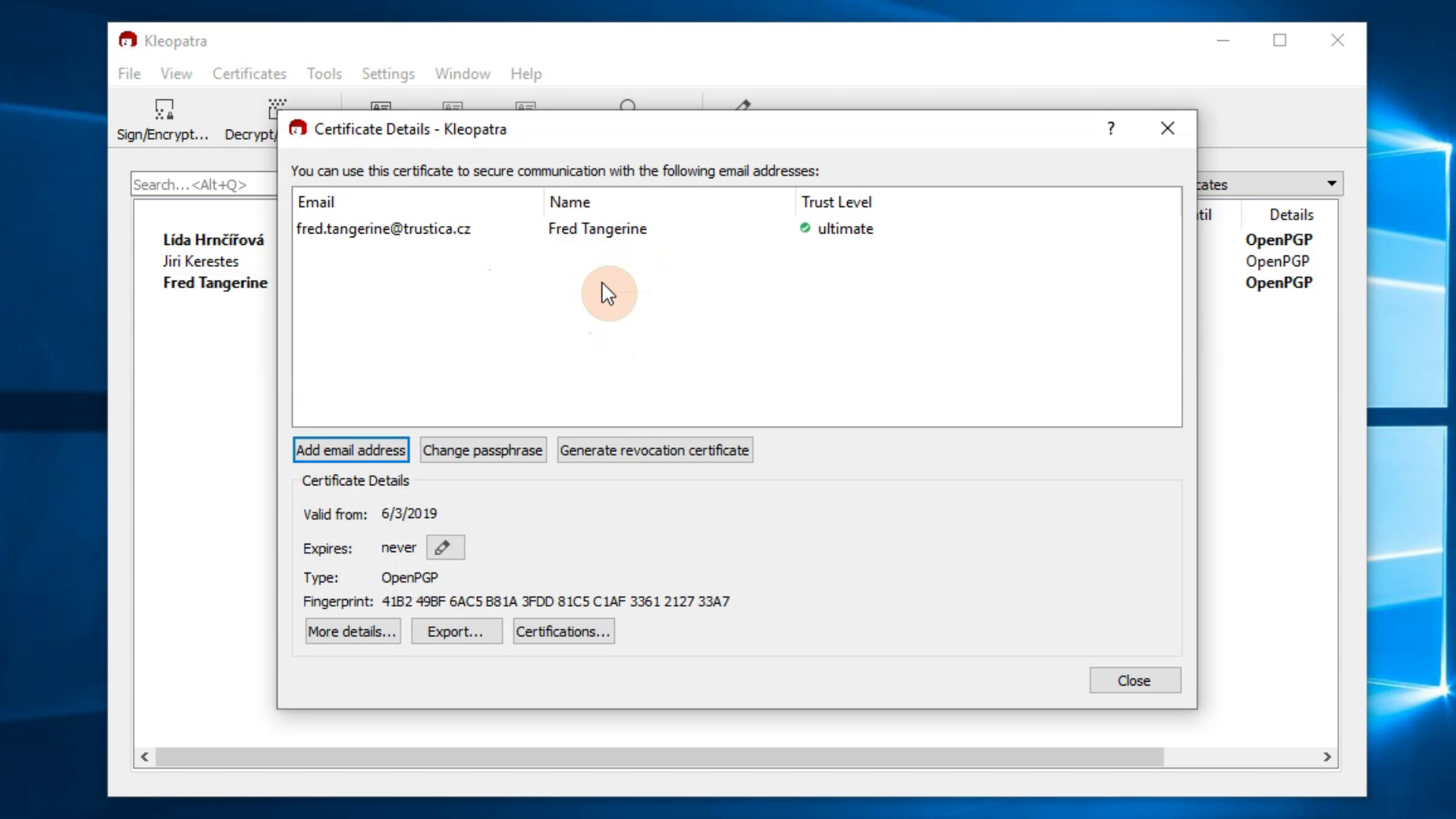
Picture 5: Key details In case you're still struggling with some of these actions, watch our instructional video:
Video 1: Cryptoucan™ usage: Key management Thank you very much for reading, we will see you next week!
