Cryptoucan™ usage: SSH setup with PuTTY on Windows
Written by Lída Hrnčířová on 2021-01-07
cryptoucanDid you know you could use Cryptoucan for remote login via SSH? It's surprisingly convenient and easy! In today's blog post we will walk you through the setting up process on Windows using PuTTY and command line - in our brand new instructional video! We've already shared a written guide on this topic, we link to it here, too!
We've already shown you all the basic operations you can do easily thanks to Cryptoucan - encrypting, decrypting, signing. Not only for emails but also files themselves... And that's still not everything you can do. Now it's time for a bit more advanced operation - authentication.
SSH is a widely used remote access protocol. It allows you to log into your remote machine's console and work there as if it was your local workstation. This is perfect for home offices or even casually working from a café. Honestly, we can see ourselves at a remote beach sipping from a drink in one hand and typing on a laptop with the other hand while listening to the calming sounds of the sea.
In this instructional video, we will show you how to set up PuTTY support in GnuPG - which will need some command line magic. But do not worry, it's super easy - as we already promised. We've got all the lines you'll need, you only have to copy and paste them at proper places, as shown in the instructions. We've put them at the bottom of this blog post.
Let's not waste any more time! Watch the video below!
Video 1: SSH setup with PuTTY on Windows We will be using PuTTY as it is one of the most popular tools for SSH access on Windows.
Commands - Setup
notepad.exe %APPDATA%\gnupg\gpg-agent.conf
enable-ssh-support
enable-putty-support
Commands - Export public SSH key
gpg -K
gpg --export-ssh-key KEYID
Commands - Mark GPG key for use with SSH
gpg -K
notepad.exe %APPDATA%\gnupg\sshcontrol
sshcontrol
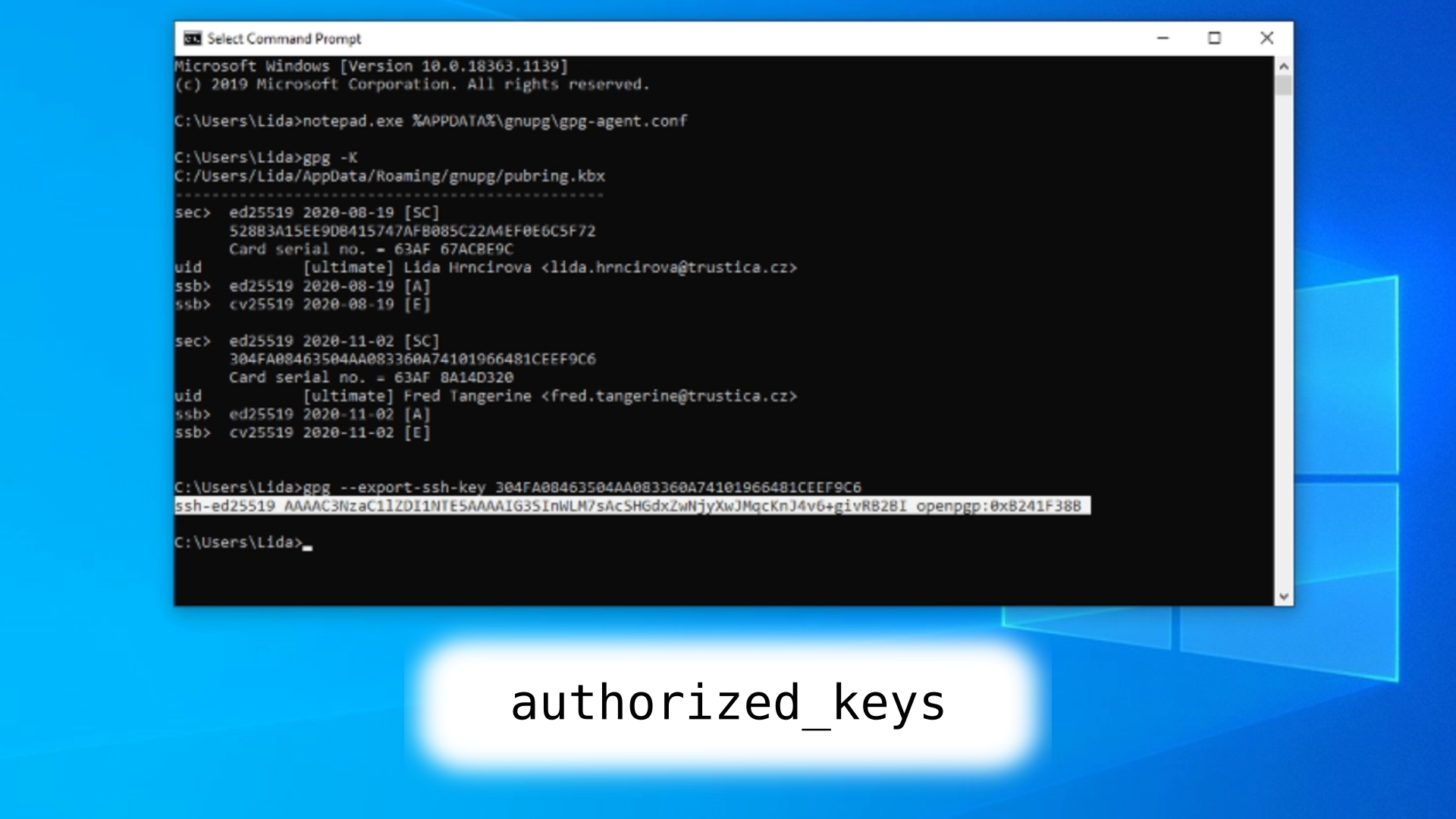
Picture 1: Newly generated public key for SSH If you're here for the link to our written guide, click here!
That's all for today's blog post! Next week we will continue by logging in!
