LinuxDays Videos are Available
Written by Dominik Pantůček on 2024-11-07
rclonelinuxAs has been announced earlier, I had the opportunity to talk about recent rclone developments at the LinuxDays conference. Although the talk started at 10AM, the auditorium was crowded and it turns out many people were actually very interested how it is possible to ensure decent confidentiality when using public cloud object storage services!
First and foremost, the video - including the rock'n'roll introduction - from the talk is out:
And also the slides are are available for download. But to get a glimpse of how it went a brief overview of the whole talk is probably appropriate.
Firstly, we have discussed what an object storage is. The key-value nature of such storage, similarities and differences to files and directories and also the typical authentication mechanisms.
After laying out the basic concepts it was possible to introduce the synchronization
tool rclone, list its basic features and compare it
to the well-known rsync tool that is used for
example for incremental data backups. Some funny moments happened as well. There was
exactly one person in the audience who never heard about backups using
rsync.
Then the encryption layer rclone provides was discussed. The key
derivation algorithm based on SCrypt
was briefly explained and the options for encrypting both data and partially meta-data
were presented. The configuration of this encryption was also covered.
The comlete encryption schema can be seen in the following picture:
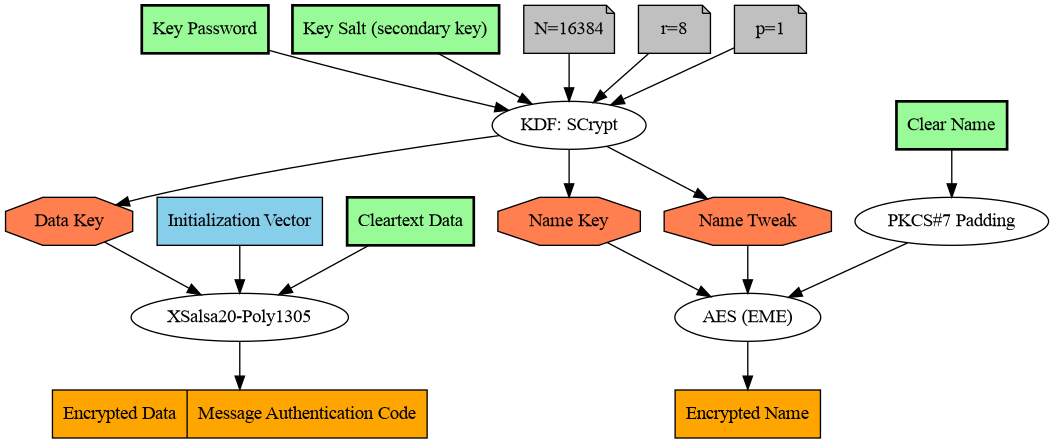
The encryption configuration is the single point where the key material and therefore all the protected confidential data might get exposed. Therefore the sensitive parts are partially obscured so that any person passing by a screen with such configuration displayed should not be able to simply memorize the contents and derive the secret keys.
However this should not be taken as any serious protection against copying the file contents or making an image of the screen. That is why we have discussed configuration encryption in detail. With the new rclone release there are multiple ways to read the password used to derive configuration encryption key. This helps both with actually protecting the secret key material and also it opens some paths for helping with sharing secret key material among multiple users within teams.
The detailed schema of the configuration encryption schema is as follows:
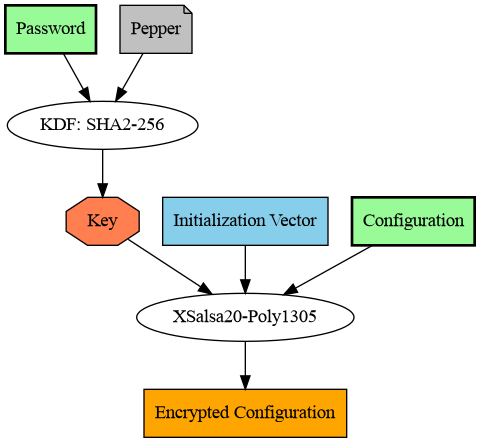
The audience apparently paid attention as the Q&A session was rather long and very informative. It was really great to see people actually interested in the topic and providing immediate feedback and valuable questions.
All in all it was a blast and big thanks should go out to all the organizers and sponsors.
If you liked it - see you next time!
