Symmetric cipher modes
Written by Dominik Joe Pantůček on 2019-03-07
cryptographyDesigning a perfect storage for your private keys is one thing. But generally speaking - using cryptography properly is much bigger challenge for the users and all the software in security ecosystem. Read on to find some interesting aspects of symmetric ciphers you might not have known about.
Most of the symmetric ciphers in use today are so-called block ciphers[1]. This might sound a little cryptic to uninformed reader but in reality this just means that the cipher uses a given key to encrypt the data in fixed-size blocks. The size of such block is what you see if you look for example at the security properties of your favorite website which typically goes along something like TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256.
Even more cryptic - isn't it? If we break this down, it is rather easy to understand. TLS[2] stands for Transport-Layer Security which is - as you might have suspected - an encryption at the transport layer. The application protocols like HTTP run inside an encrypted channel at this layer. Then the key exchange algorithm is specified - in the aforementioned case it is ECDHE: Elliptic-Curve Diffie-Hellman Ephemeral[3] key exchange. Yes, I we have a video about that one. RSA[4] is still pretty common algorithm used both for encryption and signing. In this case it is used for signing the key exchange and therefore certifying that given connection is really to the server you are attempting to communicate with. Typically RSA is used in X.509 certificates but ECDSA[5] algorithm is taking over. Another video of mine.
Then starts the interesting start with AES_128_GCM says it is AES[6] cipher in GCM[7] mode using 128-bit keys. And SHA2[8] with 256-bits of length is used for message authentication - basically a tamper protection measure to protect you against man in-the-middle[9] (MITM) attacks.
So what is this mode thing about? What about a graphical example here? Look at the Picture 1 below to see our plaintext image of Cryptoucan™.
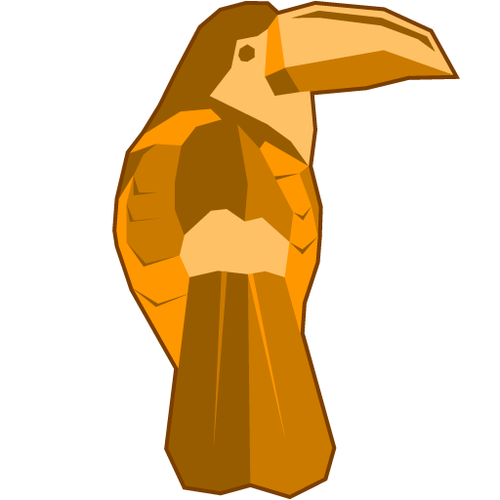
Picture 1: Clear text Cryptoucan™ image As the block cipher has to encrypt the image block-by-block - remember, in this case the blocks are 128 bits long - a naive approach might just process all the blocks of the image one by one and be done with encryption. This is called Electronic Code Book[10] (ECB) mode. You can see such encrypted image in Picture 2.
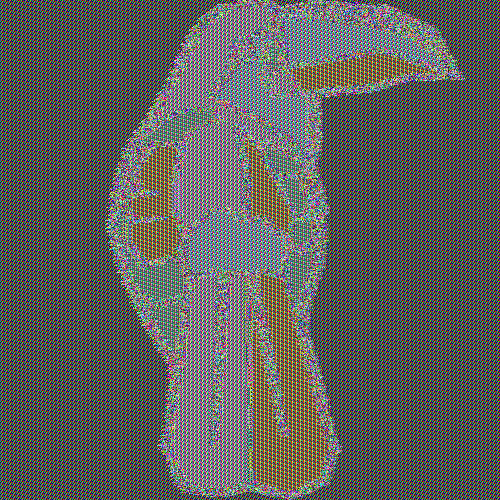
Picture 2: Encrypted image of Cryptoucan™ using AES cipher in ECB mode Well - it looks scrambled but even to an untrained eye it becomes quickly apparent that id does not hide the information completely. Actually for such simple image it reveals much more than it should.
But we can do better. We can use cipher-block chaining[11] (CBC) mode where the first block is first scrambled using an arbitrary random block called initialization vector[12] (IV) and then each following block gets first scrambled with the contents of the previous one.

Picture 3: An encrypted image of Cryptoucan™ using AES cipher in CBC mode As you can see in Picture 3, this looks truly incomprehensible and therefore we assume it is impossible to reveal what the original image was.
That is true, but it is not enough. This gives us only a protection against eavesdropping. Now what if someone had the ability to tamper with the image on-wire as it is going to our browser? Truth is that in the CBC mode if we know at least some parts of the clear text, we can modify the following ciphertext parts by destroying the immediately preceding block. And this is where Galois/counter mode (GCM) comes handy. Although the resulting image would be similar, it would be impossible for an attacker to modify parts of the encrypted message without the receiver noticing.
If you are using Cryptoucan™ with the latest versions of supported software you can be sure that your messages are encrypted with strong cipher operating in mode that ensures not only confidentiality but integrity as well. So always check if you are running the latest software! And if you are implementing your own cryptographic routines - be careful. You should know that you need to ensure much more than just the simple fact that you cannot decipher it yourself without the key. There are other attacks and there are cryptologists that can do much more if they land their hands on your messages.
Thank you for following our path to more secured communication and come back next week for more!
References
-
Wikipedia contributors. (2019, February 26). Block cipher. In Wikipedia, The Free Encyclopedia. Retrieved 21:51, March 6, 2019, from https://en.wikipedia.org/w/index.php?title=Block_cipher&oldid=885152613
-
Wikipedia contributors. (2019, February 27). Transport Layer Security. In Wikipedia, The Free Encyclopedia. Retrieved 21:51, March 6, 2019, from https://en.wikipedia.org/w/index.php?title=Transport_Layer_Security&oldid=885391142
-
https://trustica.cz/en/2018/05/17/elliptic-curve-diffie-hellman-key-exchange/
-
Wikipedia contributors. (2019, February 21). RSA (cryptosystem). In Wikipedia, The Free Encyclopedia. Retrieved 21:50, March 6, 2019, from https://en.wikipedia.org/w/index.php?title=RSA_(cryptosystem)&oldid=884347865
-
https://trustica.cz/en/2018/06/07/elliptic-curve-digital-signature-algorithm/
-
Wikipedia contributors. (2019, March 2). Advanced Encryption Standard. In Wikipedia, The Free Encyclopedia. Retrieved 21:48, March 6, 2019, from https://en.wikipedia.org/w/index.php?title=Advanced_Encryption_Standard&oldid=885783049
-
Wikipedia contributors. (2019, February 15). Galois/Counter Mode. In Wikipedia, The Free Encyclopedia. Retrieved 21:48, March 6, 2019, from https://en.wikipedia.org/w/index.php?title=Galois/Counter_Mode&oldid=883534132
-
Wikipedia contributors. (2019, February 3). SHA-2. In Wikipedia, The Free Encyclopedia. Retrieved 21:47, March 6, 2019, from https://en.wikipedia.org/w/index.php?title=SHA-2&oldid=881502942
-
Wikipedia contributors. (2019, March 6). Man-in-the-middle attack. In Wikipedia, The Free Encyclopedia. Retrieved 21:47, March 6, 2019, from https://en.wikipedia.org/w/index.php?title=Man-in-the-middle_attack&oldid=886400985
-
Wikipedia contributors. (2019, February 17). Block cipher mode of operation. In Wikipedia, The Free Encyclopedia. Retrieved 21:45, March 6, 2019, from https://en.wikipedia.org/w/index.php?title=Block_cipher_mode_of_operation&oldid=883830740#ECB
-
Wikipedia contributors. (2019, February 17). Block cipher mode of operation. In Wikipedia, The Free Encyclopedia. Retrieved 21:45, March 6, 2019, from https://en.wikipedia.org/w/index.php?title=Block_cipher_mode_of_operation&oldid=883830740#CBC
-
Wikipedia contributors. (2018, September 16). Initialization vector. In Wikipedia, The Free Encyclopedia. Retrieved 21:45, March 6, 2019, from https://en.wikipedia.org/w/index.php?title=Initialization_vector&oldid=859859805
